This is an archive version of the document. To get the most up-to-date information, see the current version.
This is an archive version of the document. To get the most up-to-date information, see the current version.Guest OS Credentials
To coordinate proper VSS and indexing activities, Veeam Backup & Replication deploys a small executable file inside a machine. It is installed only during VSS quiescence procedure and removed immediately after the processing is finished (depending on the selected option, during the backup job or after it is finished), thus producing low impact on machine performance and stability. To learn more, please refer to Veeam Backup & Replication User Guide.
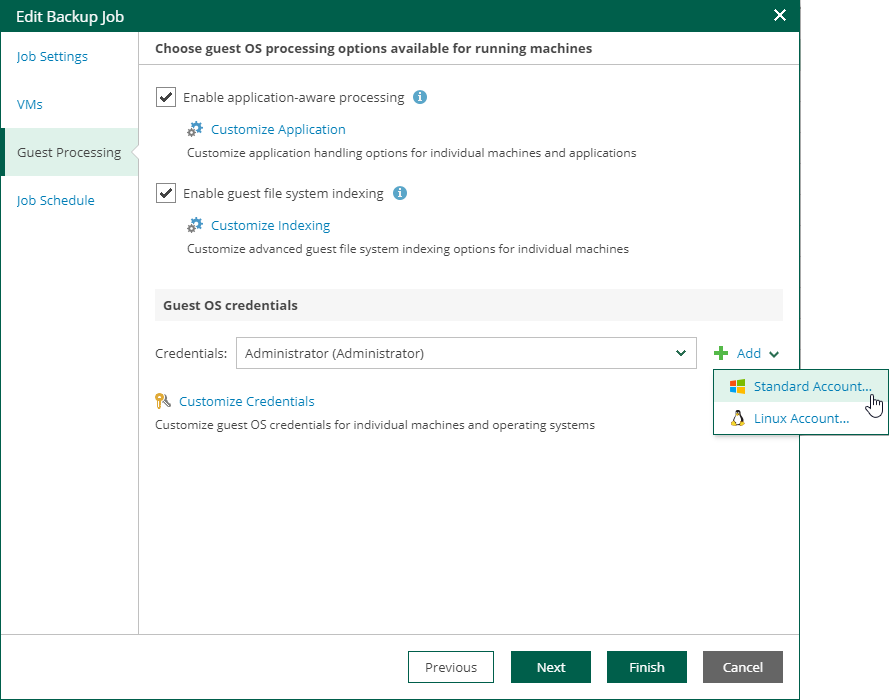
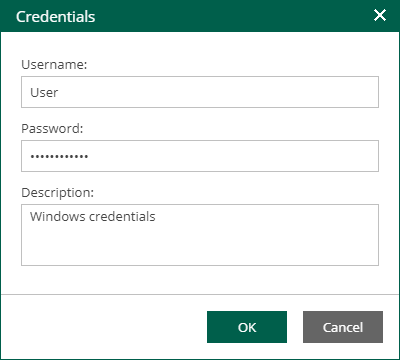
In the Guest OS credentials section, you need to specify an account with sufficient privileges for deploying this executable file on the guest OS (Windows or Linux). You can select credentials from the list, or click the Add button to add new credentials.
- For Windows guest OS, you must supply user account (name and password) with local administrative rights on target machine, and optional description. Credentials must be specified in the following format:
- For Active Directory accounts — DOMAIN\Username
- For local accounts — Username or HOST\Username
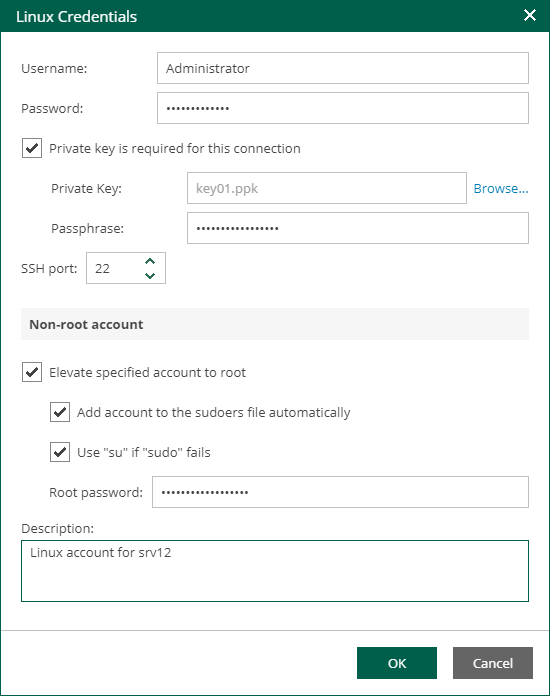
- For Linux guest OS, you must supply a user name, password, and SSH port (default is 22). Use corresponding options to elevate the specified account to root and to add it to the sudoers file automatically. In the sudoers file, enable the NOPASSWD:ALL option for the user account that you want to elevate to root (otherwise, jobs addressing a Linux server will fail as sudo will request the password). To prevent sudo from fail use the Use "su" if "sudo" fails option. In that case, if for some reason sudo fails, the specified account will be elevated to su instead.
|
For machine guest OS indexing of Linux-based machines, a user account with root privileges on the machine is required. It is recommended that you create a separate user account for work with Veeam Backup & Replication on the Linux-based machine, grant root privileges to this account and specify settings of this account in the Guest OS Credentials section. It is also recommended to avoid additional commands output for the specified user (like messages echoed from within ~/.bashrc or command traces before execution), because they may affect Linux machine processing. |
Linux Private Key
Another option is to use Linux private key. This method eliminates the need to supply password at each login, helps to protect against malicious applications like keyloggers, thus strengthening security, and simplifies launch of automated tasks, decreasing administrative load in Linux environments. For this method, a user must create a pair of keys:
- Private key is stored on the client (user’s) machine — that is, on the machine where Veeam Backup & Replication runs. The key is usually stored in the encrypted form. To decrypt a private key, you need to supply a passphrase specified at key creation.
- Public key is stored on the server (Linux machine) in a special authorized_keys file that contains a list of public keys.
If you plan to use Linux private key for authentication, make sure you have created private and public keys and stored them appropriately: private key on the client side (Veeam backup server) and public key on the server side (Linux machine). You should also have the passphrase for the private key, if it is encrypted. If you select to use Linux private key credentials, you should specify the following:
- User name
- Passphrase for private key
- Private key stored on the client side (Veeam backup server)
- SSH port (default is 22)
- Non-root account elevation options
Special Credentials for Machine
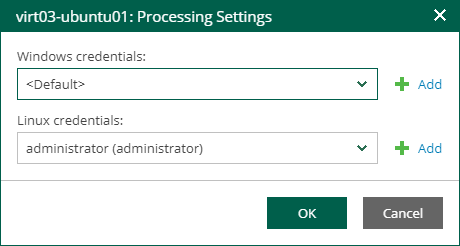
By default, for all machines in the list Veeam Backup & Replication uses common credentials you provided in the Guest OS credentials section.
- If a different account should be used to deploy the agent inside a specific machine, select the machine in the list, click Set User and enter custom guest OS credentials.
- To discard custom credentials for a machine, select it in the list and click the Remove button.
|
To customize settings of a machine added to the job as part of a container, the machine should be included in the list as a standalone instance. For that, click Add Machine and choose a machine whose settings you want to customize. |