This is an archive version of the document. To get the most up-to-date information, see the current version.
This is an archive version of the document. To get the most up-to-date information, see the current version.Veeam ONE Server Settings
The Veeam ONE Server section groups configuration settings for Veeam ONE monitoring service.
This section includes the following tabs:
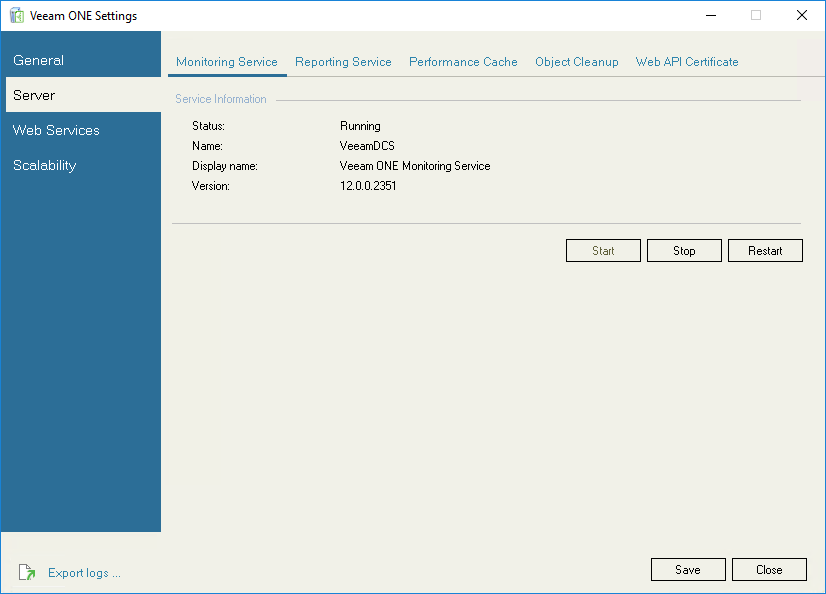
On the Monitoring Service tab, you can start, stop or restart the Veeam ONE Monitoring service. These operations may be required to complete Veeam ONE configuration updates.
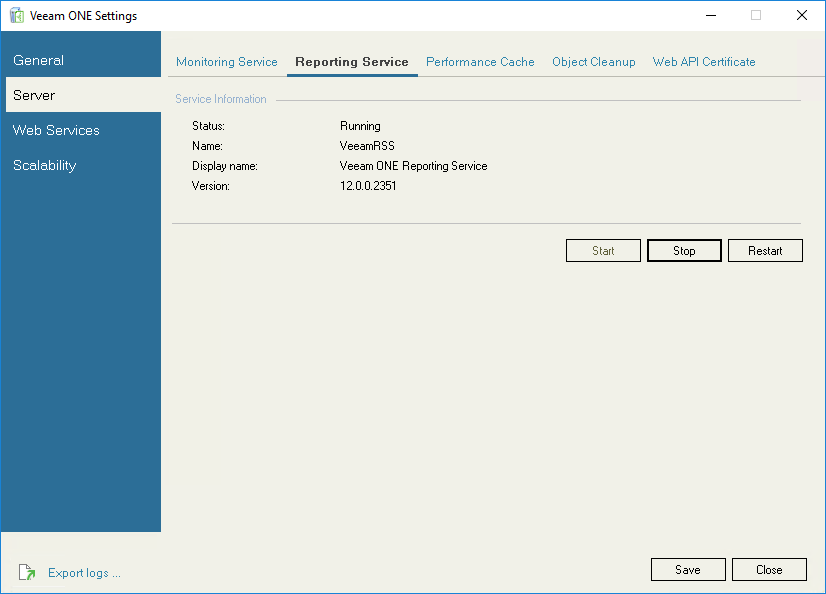
On the Reporting Service tab, you can start, stop or restart the Veeam ONE Reporting service. These operations may be required to complete Veeam ONE configuration updates.
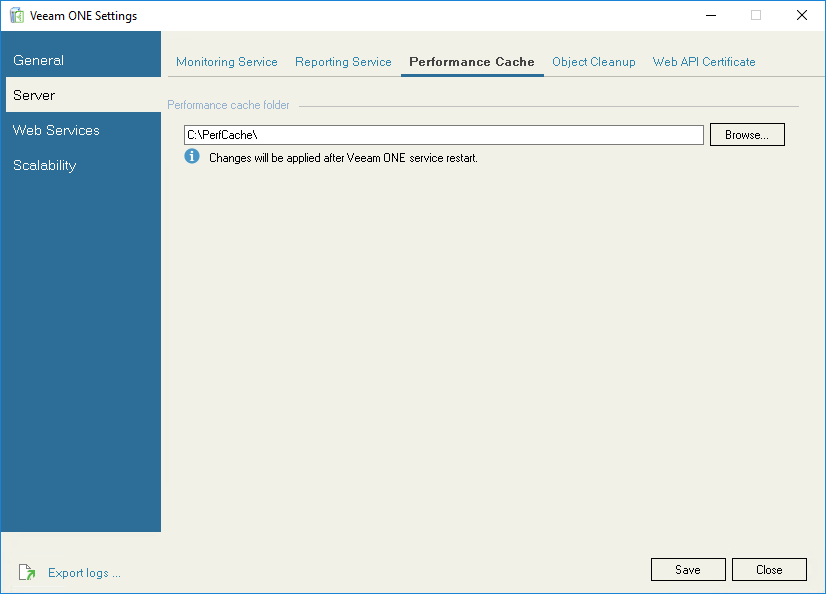
On the Performance Cache tab, you can change the path to the directory in which performance cache is stored. After you change the directory, switch to the Monitoring Service tab and restart Veeam ONE Monitoring service.
The initial directory to store performance cache is specified during installation.
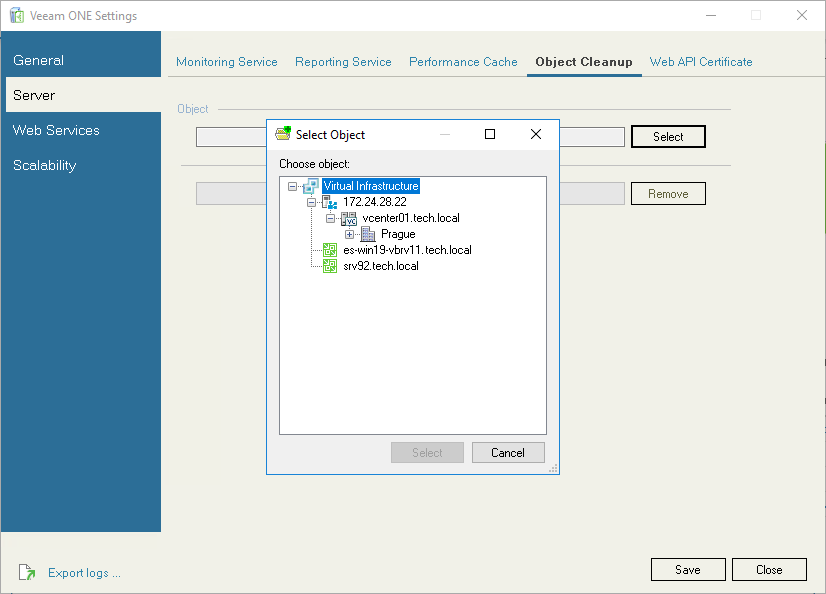
On the Object Cleanup tab, you can remove residual data on deleted infrastructure objects from the Veeam ONE database.
In some cases, data collected from infrastructure objects remain in the Veeam ONE database even if connections to these infrastructure objects are removed in the Veeam ONE Client. As a result, residual data may appear in Veeam ONE reports.
To clean data on obsolete infrastructure objects from the Veeam ONE database:
- Click Select and choose an infrastructure object for which data must be removed.
- Click Remove and wait for completion of the object data cleanup.
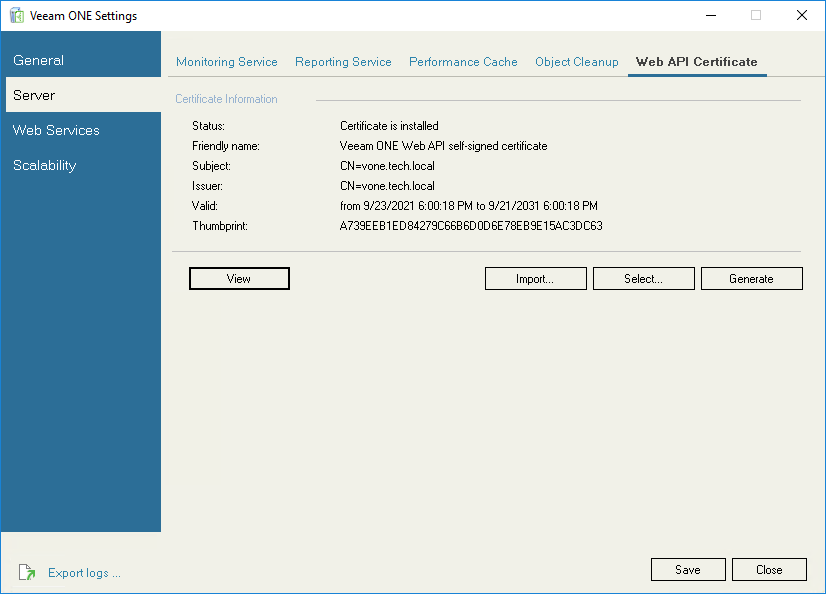
On the Web API Certificate tab, you can view and manage security certificate installed to protect connection to Veeam ONE REST API. By default Veeam ONE uses the certificate provided during installation.
- The Certificate Information section displays summary details of the currently installed certificate.
Click View, to see detailed information on the certificate.
- To import the certificate on the machine where Veeam ONE server component is installed, click Import and browse the certificate file.
- To use the certificate from the certificate store of the machine where Veeam ONE server component is installed, click Select and select the certificate from the certificate store.
- To generate a new self-signed certificate, click Generate.
Veeam ONE will generate a certificate using RSA algorithm with a 2048-bit key length and SHA-2 hashing algorithm. To use a newly generated certificate, in the displayed window, click Yes.