This is an archive version of the document. To get the most up-to-date information, see the current version.
This is an archive version of the document. To get the most up-to-date information, see the current version.Checking IAM Role Permissions
It is recommended that you run the IAM role permission check before you perform any operation to avoid the operation failure. For example, after you specify an IAM role in worker instance settings, you can check whether permissions of this IAM role are sufficient to launch worker instances. You can also run the permission check after you make changes in your AWS account and want to ensure that permissions granted to the IAM role remain sufficient.
To run the permission check for an IAM role, do the following:
- Switch to the Configuration page.
- Navigate to Accounts > IAM Roles.
- Select an IAM role and click Check AWS Permissions.
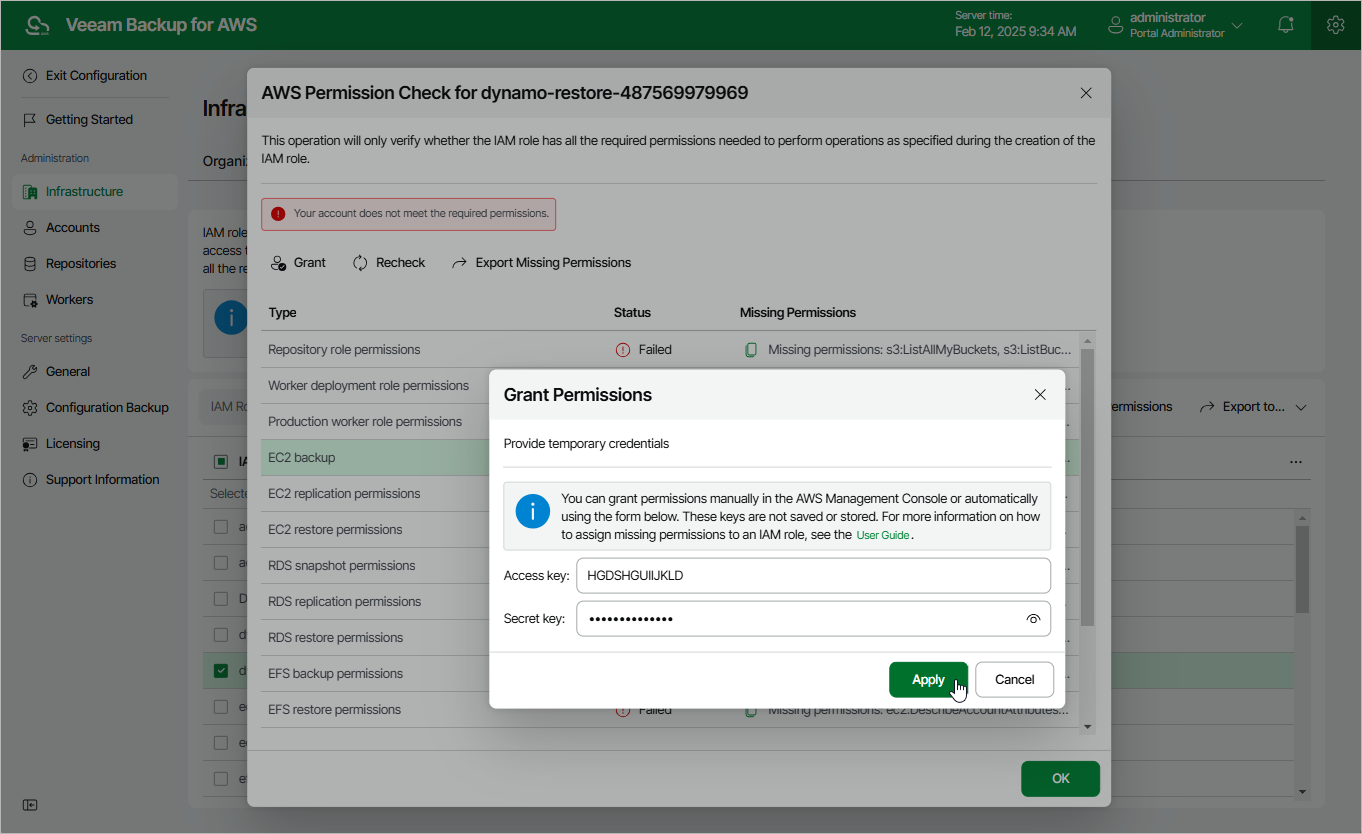
Veeam Backup for AWS will display the AWS Permission Check window where you can track the progress and view the results of the check. If the IAM role permissions are insufficient, the check will complete with errors, and the list of permissions that must be granted to the IAM role will be displayed in the Missing Permissions column. You can grant the missing permissions to the IAM role using the AWS Management Console or instruct Veeam Backup for AWS to do it.
To let Veeam Backup for AWS grant the missing permissions:
- In the AWS Permission Check window, click Grant.
- In the Grant permissions window, provide one-time access keys of an IAM user that is authorized to update permissions of IAM roles, and then click Apply.
The IAM user must have the following permissions:
"iam:AttachRolePolicy", "iam:CreatePolicy", "iam:CreatePolicyVersion", "iam:CreateRole", "iam:GetAccountSummary", "iam:GetPolicy", "iam:GetPolicyVersion", "iam:GetRole", "iam:ListAttachedRolePolicies", "iam:ListPolicyVersions", "iam:UpdateAssumeRolePolicy" |
Note |
Veeam Backup for AWS does not store one-time access keys in the configuration database. |
- To make sure that the missing permissions have been successfully granted, click Recheck.