This is an archive version of the document. To get the most up-to-date information, see the current version.
This is an archive version of the document. To get the most up-to-date information, see the current version.Step 4. Enable Data Encryption
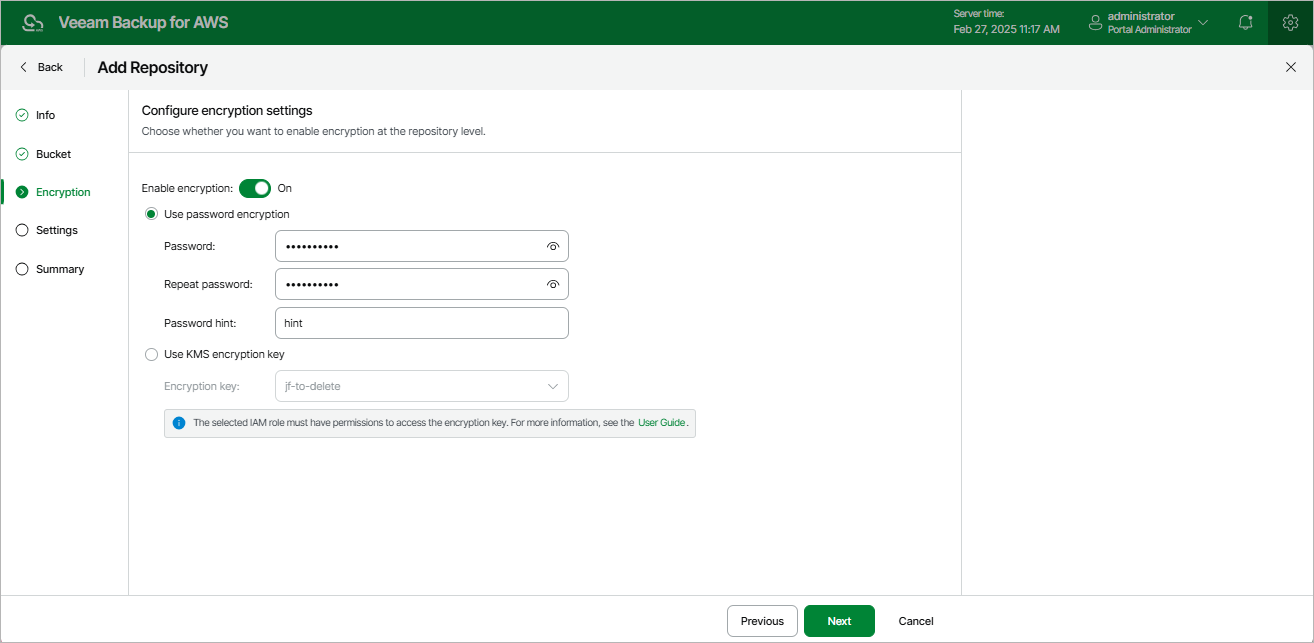
At the Options step of the wizard, choose whether you want to encrypt backup files stored in the selected Amazon S3 bucket folder.
Important |
If you have selected an existing folder at the Settings step of the wizard, and if encryption is enabled for this folder at the repository level, you must provide the currently used password or an encryption key to let Veeam Backup for AWS access this folder and add it as a backup repository. You cannot change encryption settings while adding the repository. However, you will be able to edit the repository settings later. |
To enable encryption for the backup repository, do the following:
- Click Edit Encryption Settings.
- In the Encryption settings window, set the Enable encryption toggle to On.
- Choose whether you want to use a password or an AWS Key Management Service (KMS) key to encrypt the backed-up data. For more information on encryption algorithms, see Backup Repository Encryption.
- To encrypt data using a password, select the Use password encryption option and specify the password and a password hint.
- To encrypt data using an AWS KMS key, select the Use KMS encryption key option and choose the necessary KMS key from the Encryption key drop-down list.
For a KMS key to be displayed in the list of available encryption keys, it must be created in the AWS Region where the selected Amazon S3 bucket is located, and the IAM role specified to access the bucket must have permissions to the key. For more information on permissions required for the IAM role, see Repository IAM Role Permissions.
Important |
If you select the Use KMS encryption key option, mind the following:
If a KMS key is scheduled for deletion, it will acquire the Pending deletion state. In this case, Veeam Backup for AWS will raise the warning, and, during the following 7 days, you must either change the encryption settings for the backup repository in Veeam Backup for AWS or cancel the key deletion. For more information on managing AWS KMS keys, see AWS Documentation. |