This is an archive version of the document. To get the most up-to-date information, see the current version.
This is an archive version of the document. To get the most up-to-date information, see the current version.Checking IAM Role Permissions
It is recommended that you check whether IAM roles specified to perform operations in Veeam Backup for AWS have all the required permissions — otherwise, the operations may fail to complete successfully. The check must be performed not only when you specify a new IAM role to perform an operation, but also after you make any changes in your AWS account and want to ensure that the permissions granted to the existing IAM roles remain sufficient.
You can verify IAM role permissions either using the built-in wizard permission check that is available when specifying roles for operations, or using the permission check at the IAM Roles tab.
Checking IAM Role Permissions Using Wizard Functionality
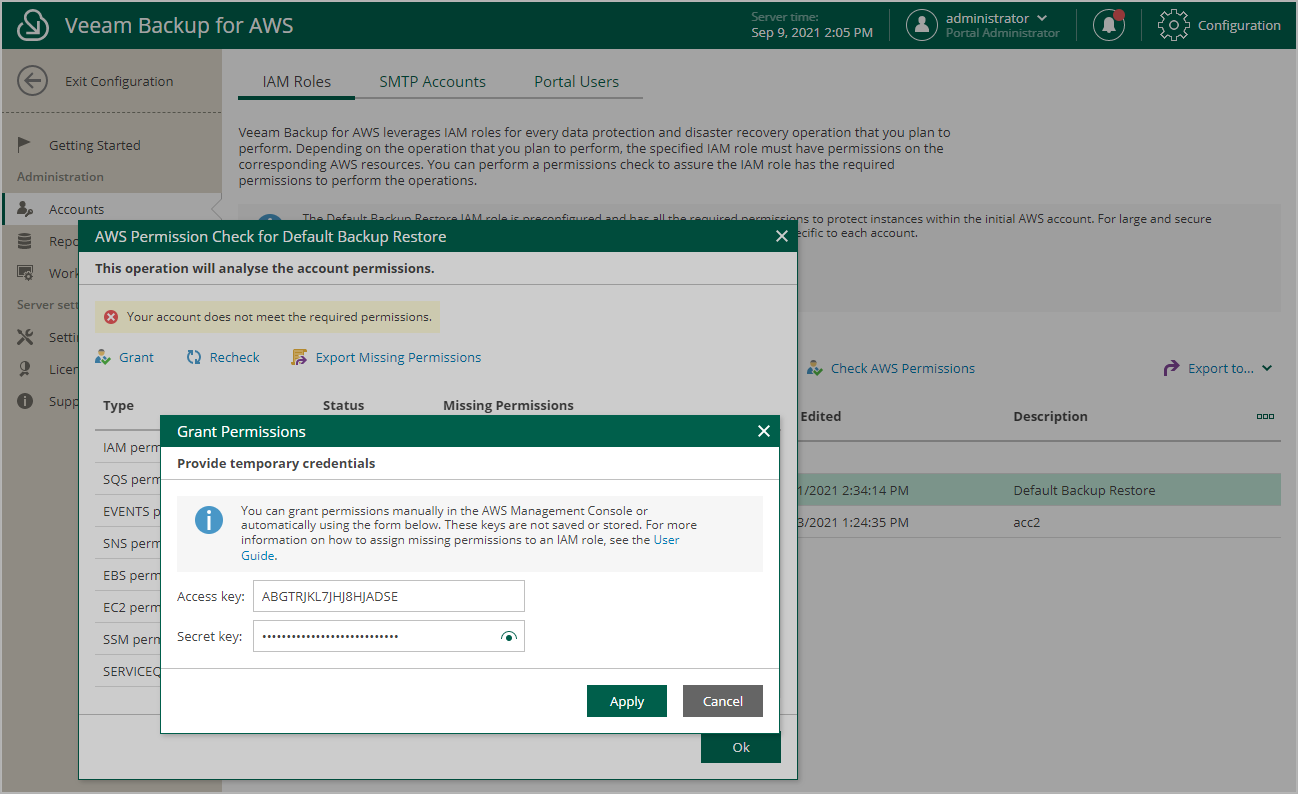
To check permissions of an IAM role specified to perform an operation, navigate to the step of the wizard at which you have selected the role, and click Check Permissions. Veeam Backup for AWS will display the Permission check window where you can track the progress and view the results of the check. If the IAM role permissions are insufficient, the check will complete with errors, and the Missing Permissions column will display the list of permissions that must be granted to the IAM role. You can grant the missing permissions to the role using the AWS Management Console or instruct Veeam Backup for AWS to do it.
Tip |
To download the full list of missing permissions as a single JSON policy document that you can use to grant the permissions to the role in the AWS Management Console, click Export Missing Permissions. |
To let Veeam Backup for AWS grant the missing permissions:
- In the Permission check window, click Grant.
- In the Grant Permissions window, provide one-time access keys of an IAM user that is authorized to update permissions of IAM roles, and then click Apply.
The IAM user must have the following permissions:
"iam:AttachRolePolicy", "iam:CreatePolicy", "iam:CreatePolicyVersion", "iam:CreateRole", "iam:GetAccountSummary", "iam:GetPolicy", "iam:GetPolicyVersion", "iam:GetRole", "iam:ListAttachedRolePolicies", "iam:ListPolicyVersions", "iam:SimulatePrincipalPolicy", "iam:UpdateAssumeRolePolicy" |
Note |
Veeam Backup for AWS does not store one-time access keys in the configuration database. |
- To make sure that the missing permissions have been granted successfully, click Recheck.
Important |
If your organization uses service control policies (SCPs) to manage permissions in its accounts, and some of the permissions required for an operation are forbidden by these SCPs, Veeam Backup for AWS will not be able to perform the operation even if you grant the permissions to the selected IAM role. For more information on SCPs, see AWS Documentation. |
Checking IAM role Permissions Using IAM Role Tab
If you are not sure whether an IAM role is currently used to perform any operations and want to check permission for this IAM role, you can use the permission check at the IAM Roles tab. This permission check can also be used for the Default Backup Restore IAM role.
To run the permission check for an IAM role, do the following:
- Switch to the Configuration page.
- Navigate to Accounts > IAM Roles.
- Select the necessary IAM role and click Check AWS Permissions.
Veeam Backup for AWS will verify whether the IAM role is currently used to perform any operations (for example, if the role is specified in the settings of a backup policy) and check if all the permissions required to perform these operations are assigned to the role.
Important |
Veeam Backup for AWS does not verify the permissions of IAM roles that are not specified in any settings on the backup appliance and are not used to perform any operations. |
You can track the progress and view the results of the permission check in the AWS Permission Check window. If the IAM role permissions are insufficient, the check will complete with errors, and the Missing Permissions column will display the list of permissions that must be granted to the IAM role. You can grant the missing permissions to the IAM role using the AWS Management Console or instruct Veeam Backup for AWS to do it.
Tip |
To download the full list of missing permissions as a single JSON policy document that you can use to grant the permissions to the role in the AWS Management Console, click Export Missing Permissions. |
To let Veeam Backup for AWS grant the missing permissions:
- In the AWS Permission Check window, click Grant.
- In the Grant permissions window, provide one-time access keys of an IAM user that is authorized to update permissions of IAM roles, and then click Apply.
The IAM user must have the following permissions:
"iam:AttachRolePolicy", "iam:CreatePolicy", "iam:CreatePolicyVersion", "iam:CreateRole", "iam:GetAccountSummary", "iam:GetPolicy", "iam:GetPolicyVersion", "iam:GetRole", "iam:ListAttachedRolePolicies", "iam:ListPolicyVersions", "iam:SimulatePrincipalPolicy", "iam:UpdateAssumeRolePolicy" |
Note |
Veeam Backup for AWS does not store one-time access keys in the configuration database. |
- To make sure that the missing permissions have been granted successfully, click Recheck.