When you configure the Veeam Agent management infrastructure in Veeam Backup & Replication, you can specify what TLS certificate Veeam Backup & Replication will use to establish a secure connection between the backup server and protected computers. By default, Veeam Backup & Replication offers the following security settings for testing and evaluation purposes:
- To establish a secure connection between parties, Veeam Backup & Replication uses the default self-signed certificate.
- Veeam Backup & Replication allows all computers that run a Linux OS to establish a connection to the backup server.
You can change security settings if needed, for example, in case security regulations of your organization require usage of a custom certificate and/or verification of Linux host fingerprints.
To specify the security settings, do the following:
- From the main menu, select General Options.
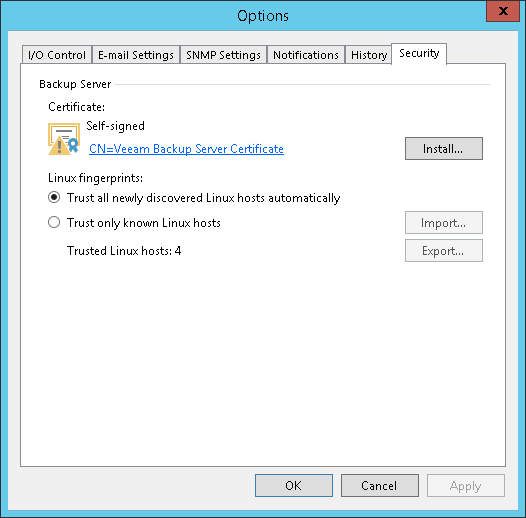
- Click the Security tab.
- In the Certificate section, check information about the currently used certificate. By default, Veeam Backup & Replication uses a self-signed TLS certificate generated at the process of upgrade to version 9.5 Update 3. If you want to use a custom certificate, click Install and specify a new certificate. To learn more, see Managing TLS Certificates.
- In the Linux fingerprints section, specify SSH fingerprint verification settings for Linux-based protected computers. You can select one of the following options:
- Trust all newly discovered Linux hosts automatically — with this option enabled, Veeam Backup & Replication allows all discovered computers that run a Linux OS to connect to the backup server. This scenario is recommended for demo environments only.
- Trust only known Linux hosts — with this option enabled, only the following Linux-based computers can connect to the backup server:
- Protected computers that have already established a connection to the backup server and have their fingerprints stored in the Veeam Backup & Replication database. Veeam Backup & Replication displays the number of such computers in the Trusted Linux hosts field. To export the list of trusted Linux computers to a known_hosts file, click Export and specify a path to the folder to save the file.
- Protected computers specified in the known_hosts file imported to Veeam Backup & Replication. To import a known_hosts file, click Import and specify a path to the folder where the file resides.
Computers that do not meet the above-mentioned conditions cannot connect to the Veeam backup server and download Veeam Agent for Linux installation packages during discovery. Veeam Backup & Replication displays these computers under the Untrusted node in the inventory. To start managing an untrusted computer, you need to validate its fingerprint manually in the Veeam Backup & Replication console. To learn more, see Validating SSH Fingerprints.
- Click OK.