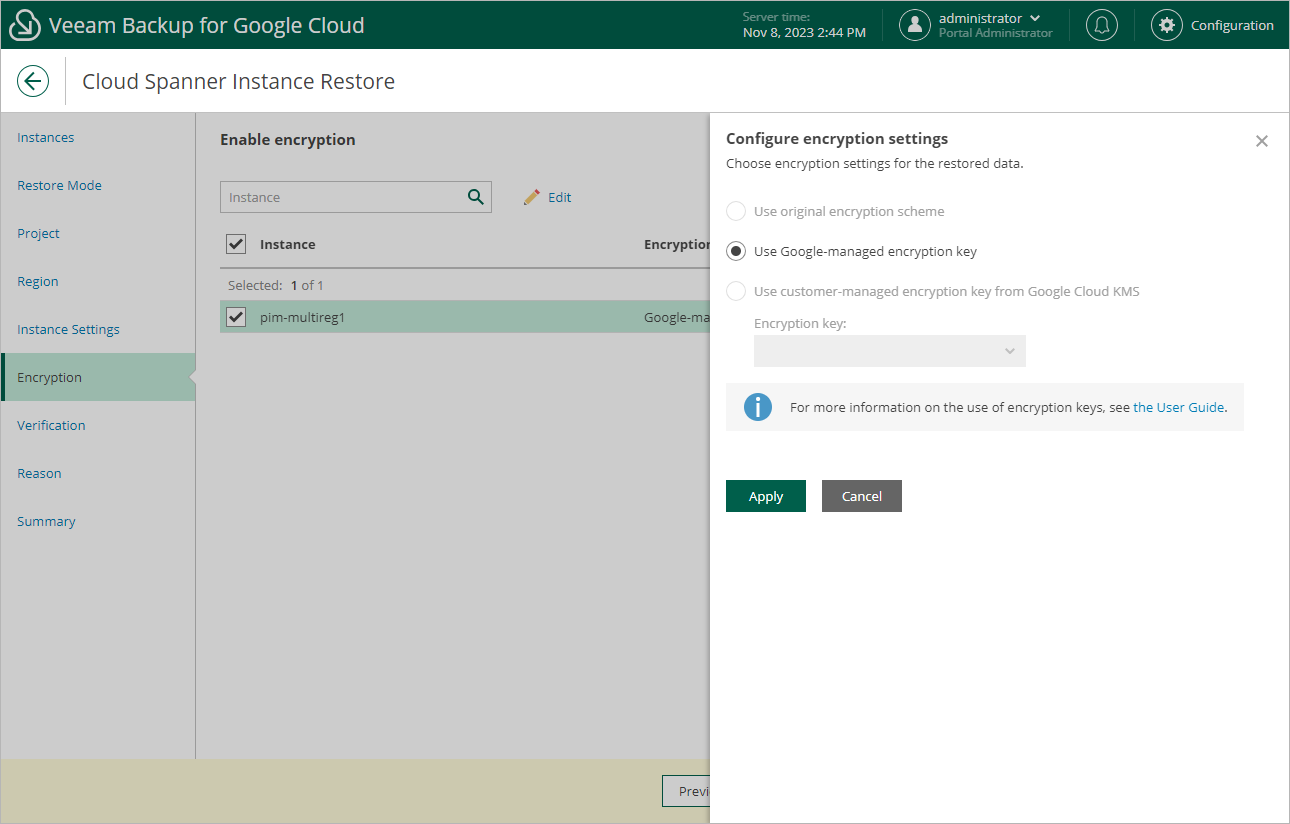
Step 8. Configure Encryption Settings
[This step applies only if you have selected the Restore to new location, or with different settings option at the Restore Mode step of the wizard]
At the Encryption step of the wizard, do the following:
- Select the Cloud Spanner instance.
- Click Edit.
- In the opened window, choose whether you want the instance data to be encrypted with a Google Cloud KMS CMEK:
- If you want to apply the existing encryption scheme of the source Cloud Spanner instance, select the Use original encryption scheme option.
- If you want to apply Google-managed encryption scheme, select the Use Google-managed encryption key option.
- If you want to encrypt the restored data with a CMEK, select the Use customer-managed encryption key from Google Cloud KMS option and choose the necessary CMEK from the Encryption key drop-down list.
For a CMEK to be displayed in the list of available encryption keys, it must be stored in the region selected at step 6 of the wizard.
Notes |
|