Adding Computers to Trusted Hosts List
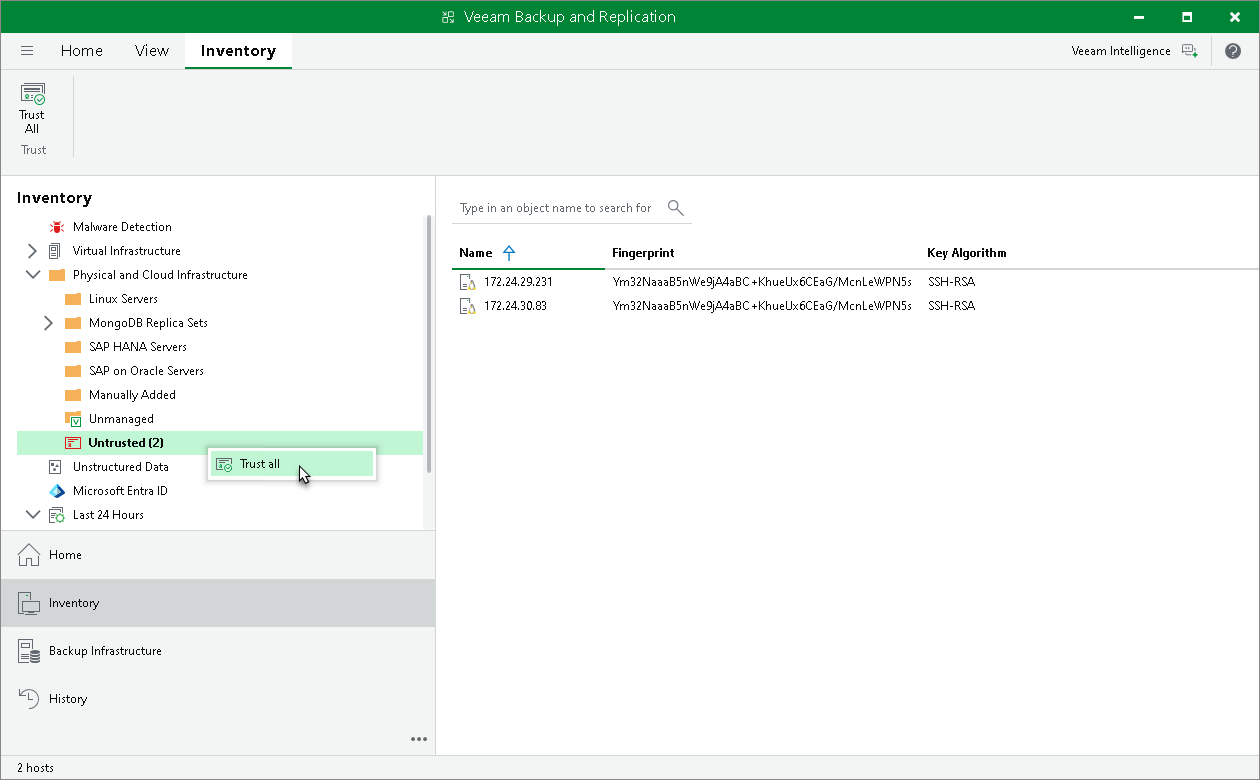
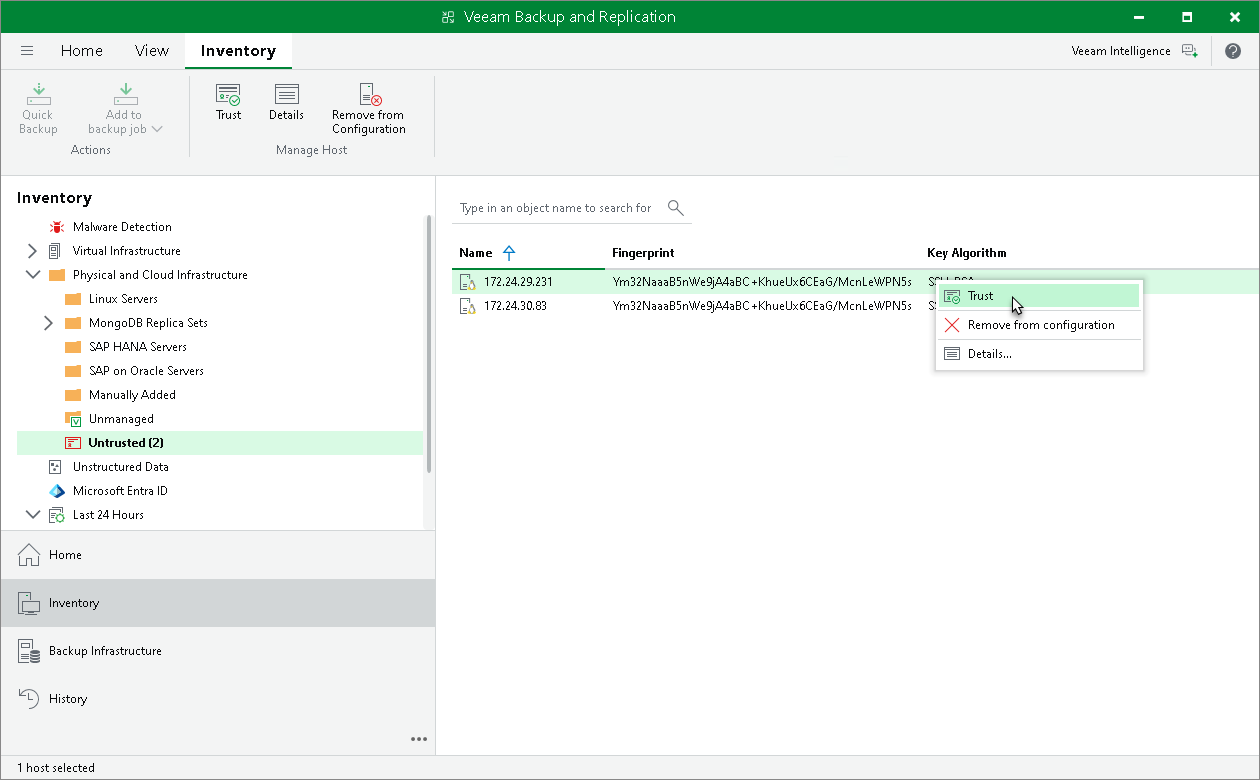
After you enable the Add unknown hosts to the list manually (more secure) option in Veeam Backup & Replication settings, Linux-based computers whose SSH fingerprints are not stored in the Veeam Backup & Replication database become unable to communicate to the Veeam backup server. During discovery, Veeam Backup & Replication puts such computers to the Untrusted protection group. To start managing an untrusted computer, you must manually validate the SSH fingerprint and add the computer to the list of trusted hosts in the Veeam Backup & Replication console.
To add a computer to the list of trusted hosts:
- Open the Inventory view.
- In the inventory pane, expand the Physical Infrastructure node and click Untrusted.
- In the working area, Veeam Backup & Replication will display discovered computers that you can add to the list of trusted hosts. Check SSH fingerprints of the computers and add them to the list of trusted hosts in one of the following ways:
- To add all computers at once to the list of trusted hosts, select the Untrusted node in the inventory pane and click Trust All on the ribbon or right-click the Untrusted node and select Trust all.
- To add a specific computer to the list of trusted hosts, select the necessary computer in the working area and click Trust on the ribbon or right-click the computer and select Trust.