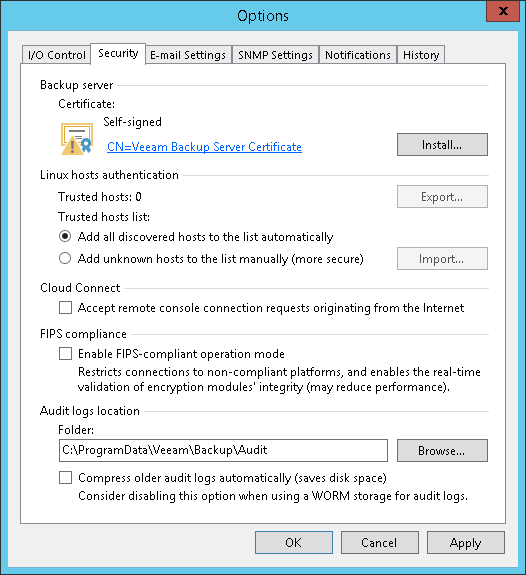
Linux主机身份验证
In the Linux hosts authentication section of the Veeam Backup & Replication settings, you can specify SSH fingerprint verification settings for protected Linux machines.
You can select one of the following options:
- Add all discovered hosts to the list automatically — with this option enabled, Veeam Backup & Replication allows all added Linux VMs and Linux servers to connect to the backup server.
- Add unknown hosts to the list manually (more secure) — with this option enabled, only the following Linux machines can connect to the backup server:
- Protected machines that have already established a connection to the backup server and have their fingerprints stored in the Veeam Backup & Replication database.
Veeam Backup & Replication displays the number of trusted machines in the Trusted hosts field. To export the list of trusted machines to the known_hosts file, click Export and specify a path to the folder to save the file.
- Protected machines specified in the known_hosts file imported to Veeam Backup & Replication. To import the known_hosts file, click Import and specify a path to the folder where the file resides.
Machines that do not meet the above-mentioned conditions cannot connect to the Veeam backup server and download Veeam Agent for Linux installation packages during discovery. Also, guest OS processing of untrusted VMs will fail.
Veeam Backup & Replication displays these computers under the Untrusted node in the inventory. To start managing an untrusted computer, you need to validate its fingerprint manually in the Veeam Backup & Replication console. To learn more, see Validating SSH Fingerprints.