Configuring SAML Authentication Settings
Organizations who use single sign-on (SSO) in their IT infrastructure can allow users to access the Veeam Backup Enterprise Manager website and vSphere Self-Service Backup Portal with their SSO credentials. To do this, the Enterprise Manager administrator must configure SAML authentication settings.
Note |
If SAML authentication is enabled, users can log in to vSphere Self-Service Backup Portal under SSO accounts only. |
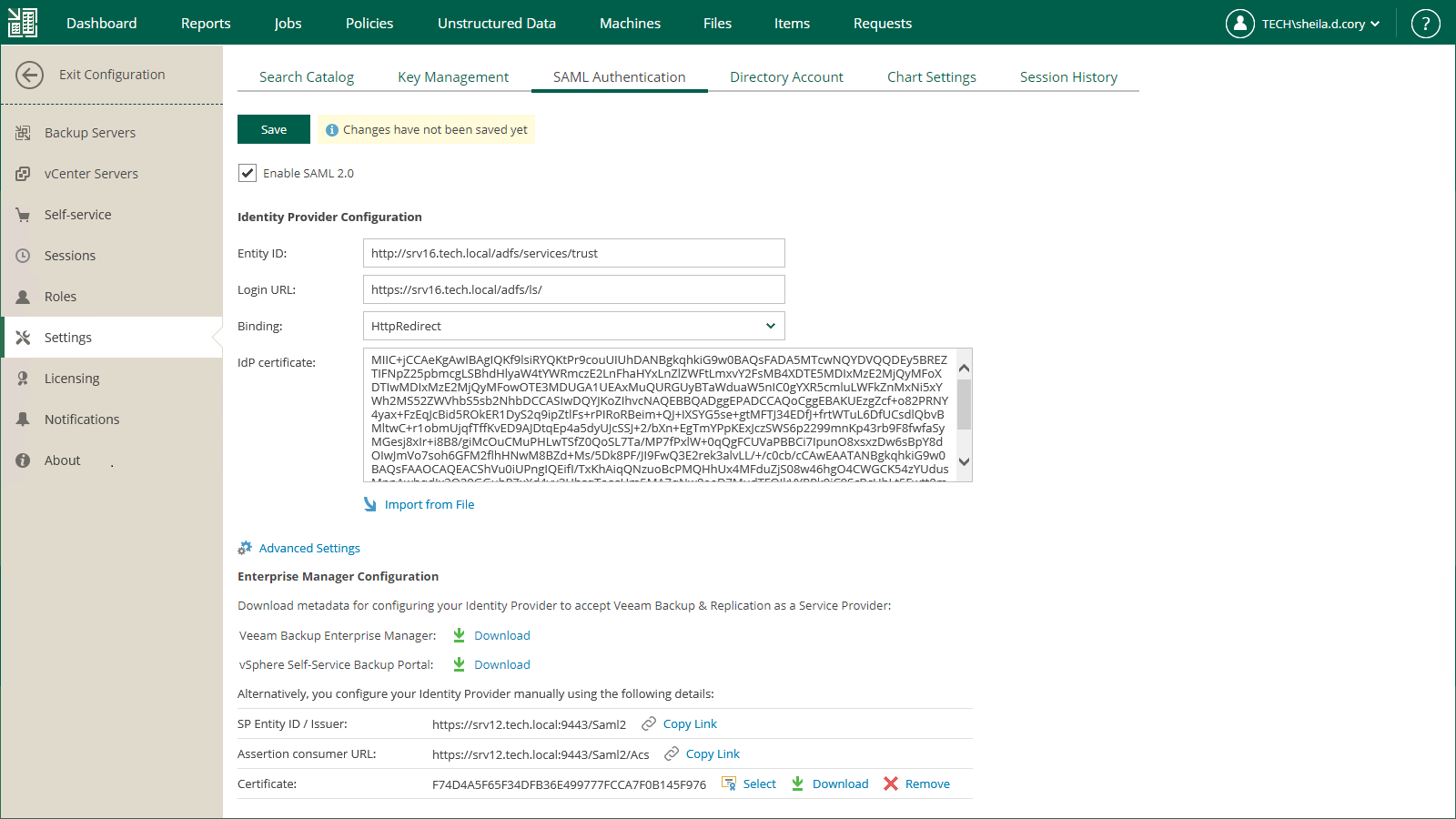
To configure SAML authentication settings:
- Log in to Enterprise Manager using an administrative account.
- To open the Configuration view, click Configuration in the top right corner.
- Open the Settings section on the left of the Configuration view.
- Click the SAML Authentication tab.
- Select the Enable SAML 2.0 option.
- In the Identity Provider Configuration section, specify identity provider settings. For more information, see Specifying Identity Provider Settings.
- [Optional] If you want to use a certificate to encrypt and sign service provider SAML requests, specify certificate settings. For more information, see Selecting Service Provider Certificate.
- [Optional] Click the Advanced Settings link and specify advanced SAML authentication settings. For more information, see Specifying Advanced SAML Authentication Settings.
- In the Enterprise Manager Configuration section, export or manually copy metadata of the service provider (the Veeam Backup Enterprise Manager website, vSphere Self-Service Backup Portal, or both) for which you configure SSO. Use the metadata to register the service provider on the identity provider side. For more information, see Obtaining Service Provider Settings.
- Click Save.
After you configure SAML authentication settings, you can register user accounts that will be able to log in to the Veeam Backup Enterprise Manager website or vSphere Self-Service Backup Portal using SSO. For more information, see Configuring Accounts and Roles and Managing Tenant Accounts.
Specifying Identity Provider Settings
To set up SAML authentication, you must obtain SAML authentication settings from the identity provider and specify them in Enterprise Manager. You can specify identity provider settings in one of the following ways:
- Import identity provider settings from a SAML metadata file obtained from the identity provider.
- Specify identity provider settings manually.
To import identity provider settings from the SAML metadata file, in the Identity Provider Configuration section of the SAML Authentication view, click the Import from File link and browse to the metadata file. The metadata file structure must conform to the SAML 2.0 Metadata Schema.
Alternatively, you can specify identity provider settings manually:
- In the Identity Provider Configuration section, in the Entity ID field, specify a unique ID of the identity provider.
- In the Login URL field, specify the URL of the single sign-on login page provided by the identity provider.
- From the Binding list, select a SAML binding used by the identity provider to send SAML responses: HttpRedirect or HttpPost.
- In the IdP certificate field, specify a certificate that will be used to validate the signature of the signed authentication assertions and decrypt assertions sent by the identity provider.
Note |
Veeam Backup Enterprise Manager does not support identity provider certificate rollover. |
Selecting Service Provider Certificate
If you want to sign and encrypt authentication requests sent from Veeam Backup Enterprise Manager to the identity provider, you must select a certificate with a private key that will be used for encryption and signing. To select a certificate:
- In the Enterprise Manager Configuration section of the SAML Authentication view, click the Select link next to the Certificate field.
- In the Select Service Provider Certificate window, Veeam Backup Enterprise Manager will display certificates located in the certificate store on the Enterprise Manager server. Choose the necessary certificate from the list and click Select.
If you use a certificate to sign end encrypt SAML authentication requests, you must pass the public key certificate to the identity provider. The identity provider will use this certificate to encrypt requests and validate the request signature. For more information, see Obtaining Service Provider Settings.
Tip |
Consider the following:
|
Specifying Advanced SAML Authentication Settings
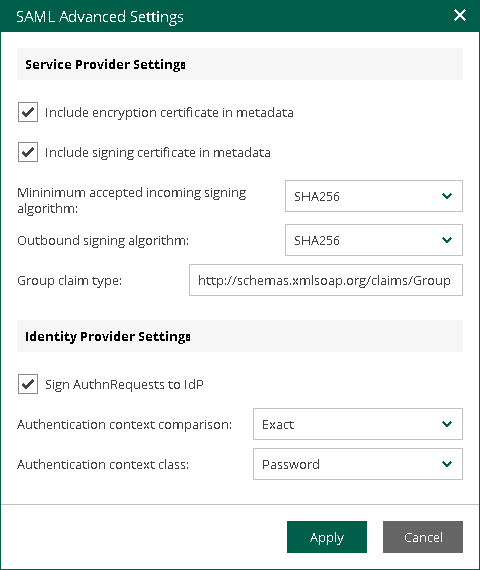
In the SAML Advanced Settings window you can specify advanced settings for SAML authentication.
- To include in the service provider SAML metadata a security certificate required to decrypt service provider authentication requests, select the Include encryption certificate in metadata check box.
- To validate the signature of the signed requests, select the Include signing certificate in metadata check box.
- From the Minimum accepted incoming signing algorithm and Outbound sign algorithm lists, select what type of signed requests and responses Enterprise Manager will be able to send and receive. By default, the SHA256 option is selected. With this option selected, Enterprise Manager will send and receive requests and responses signed using the SHA256 or stronger algorithm.
- By default, to provide for single sign-on authentication for groups of users, Veeam Backup Enterprise Manager accepts information about groups from the identity provider in statements of the Group type. If it is required to use for this purpose statements of a different type, in the Group claim type field, specify the necessary type.
- If you want to sign authentication requests sent from Enterprise Manager to the identity provider with a digital certificate, in the Identity Provider Settings section, select the Sign AuthnRequests to IdP check box.
- From the Authentication context comparison list, select a comparison method for authentication context: Exact, Minimum, Maximum or Better.
- From the Authentication context class list, select one of the classes to specify an authentication method used by the Identity Provider. For example, for VMware Platform Services Controller, select PasswordProtectedTransport. By default, the Password option is selected.
- Click Apply.
Obtaining Service Provider Settings
To set up SAML authentication for the Veeam Backup Enterprise Manager website and vSphere Self-Service Backup Portal, you need to register each of them individually as a service provider on the identity provider side. To do this, you need to obtain service provider settings and pass them to the identity provider.
You can obtain service provider settings in one of the following ways:
Exporting Service Provider Settings
You can export settings of each service provider to a SAML metadata file — an XML file that conforms to the SAML 2.0 Metadata Schema. If you plan to use a certificate to sign end encrypt SAML authentication requests, and need to pass the public key certificate to the identity provider, you must include the certificate in the metadata file. For more information, see Specifying Advanced SAML Authentication Settings.
- To export service provider settings of the Veeam Backup Enterprise Manager website, click the Download link next to the Veeam Backup Enterprise Manager field.
- To export service provider settings of vSphere Self-Service Backup Portal, click the Download link next to the vSphere Self-Service Backup Portal field.
Copying Service Provider Settings
To copy service provider settings:
- Copy the links next to the SP Entity ID / Issuer and Assertion consumer URL fields.
- If you have selected a certificate that will be used to sign end encrypt SAML authentication requests, you must also pass the public key certificate to the identity provider. To copy the certificate, click the Download link next to the Certificate field.
Related Topics