 This is an archive version of the document. To get the most up-to-date information, see the current version.
This is an archive version of the document. To get the most up-to-date information, see the current version.Data Encryption
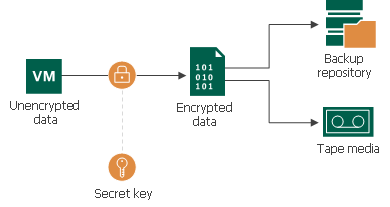
Data security is an important part of the backup strategy. You must protect your information from unauthorized access, especially if you back up sensitive VM data to off-site locations or archive it to tape. To keep your data safe, you can use data encryption.
Data encryption transforms data to an unreadable, scrambled format with the help of a cryptographic algorithm and a secret key. If encrypted data is intercepted, it cannot be unlocked and read by the eavesdropper. Only intended recipients who know the secret key can reverse encrypted information back to a readable format.
In Veeam Backup & Replication, encryption works at the following levels:
- Backup job
- Transaction log backup job
- Backup copy job
- VeeamZIP
- Tapes in media pools
Veeam Backup & Replication uses the block cypher encryption algorithm. Encryption works at the source side. Veeam Backup & Replication reads VM or file data, encodes data blocks, transfers them to the target side in the encrypted format and stores the data to a file in the backup repository or archives the data to tape. Data decryption is also performed on the source side: Veeam Backup & Replication transfers encrypted data back to the source side and decrypts it there.
Note |
Veeam Backup & Replication will pass encryption keys to the target backup repository or cloud repository in the following cases:
|
Beside the job-level encryption, Veeam Backup & Replication allows you to encrypt network traffic going between the primary site and the disaster recovery site. Network traffic encryption is configured as part of global network traffic rules that are set for backup infrastructure components. For network traffic encryption, Veeam Backup & Replication uses the 256-bit Advanced Encryption Standard (AES).
Data Encryption and Deduplication
Data encryption has a negative effect on the deduplication ratio if you use a deduplicating storage appliance as a target. Veeam Backup & Replication uses different encryption keys for every job session. For this reason, encrypted data blocks sent to the deduplicating storage appliances appear as different though they may contain duplicate data. If you want to achieve a higher deduplication ratio, you can disable data encryption. If you still want to use encryption, you can enable the encryption feature on the deduplicating storage appliance itself.
Data Encryption and Compression
If data compression and data encryption are enabled for a job, Veeam Backup & Replication compresses VM data first and after that encodes the compressed data blocks. Both operations are performed at the source side.
Note, however, that if the Decompress backup data blocks before storing check box is selected in the backup repository settings, Veeam Backup & Replication does not compress VM data before encryption. Therefore, in the job statistics, you may observe a higher amount of transferred data (the Transferred counter) as compared to a job for which encryption is disabled. For details on job statistics, see Viewing Real-Time Statistics.
In This Section