Configuring UEFI Secure Boot
When you install Veeam Agent on a UEFI system with Secure Boot enabled, you must configure the UEFI Secure Boot to allow your system to run Veeam Agent and perform backups. You do this by enrolling the Machine Owner Key (MOK) for the Veeam kernel module in your system's firmware.
To enroll MOK, perform the following steps:
- Request enrollment of the key. For pre-built kernel modules, the key is provided by Veeam; for DKMS kernel modules, the key is generated by DKMS:
- [Pre-built kernel module] To make UEFI system with Secure Boot work with pre-built Veeam kernel module, Veeam Agent requires Veeam public key to be enrolled to the system's MOK list. For more information on requesting enrollment of the Veeam kernel module key to your system, see Importing MOK for Pre-Built Kernel Module.
- [DKMS kernel module] When you install Veeam Agent, DKMS generates a Machine Owner Key that allows third-party modules to be run on the system's firmware. Such key must also be enrolled to the system's MOK list. For more information on requesting enrollment of the key for the Veeam DKMS module, see Importing MOK for Veeam DKMS Module.
NOTE |
If UEFI system with Secure Boot enabled does not support automatic generation of the key for DKMS modules, you must either sign the Veeam kernel module yourself and enroll the Machine Owner Key to your system or disable Secure Boot. |
- Enroll the key using MOK management. For more information, see Enrolling MOK.
Importing MOK for Pre-Built Kernel Module
The Veeam kernel module key is provided within the veeam-ueficert package that resides in the Veeam software repository.
When you install the veeam-ueficert package, the Veeam kernel module key is imported into your system. Depending on how you install Veeam Agent — in the online or offline mode, installation of the veeam-ueficert package may vary.
If you install Veeam Agent for Linux by mounting the Veeam software repository directly on your Linux computer, install the veeam-ueficert package by using one of the following commands:
For RHEL / Rocky Linux / AlmaLinux
yum install veeam-ueficert |
For SLES
zypper in veeam-ueficert |
If your Linux computer is not connected to the internet and you install Veeam Agent for Linux in the offline mode, to install the veeam-ueficert package and import MOK, do the following:
- Download the veeam-ueficert package for your Linux distribution version from the Veeam software repository.
- [For RHEL, AlmaLinux and Rocky Linux] The veeam-ueficert package is located in the /backup/linux/agent/rpm/<Linux distr>/<ver>/x86_64/ directory, where <Linux distr> is the name of your Linux distribution and <ver> is your Linux OS version. For example, to download the veeam-ueficert package for RHEL 10, navigate to the /backup/linux/agent-13/rpm/el/10/x86_64/ directory.
- [For SLES] The veeam-ueficert package is located in the /backup/linux/agent/rpm/<Linux distr>/<ver>/noarch/ directory, where <Linux distr> is the name of your Linux distribution and <ver> is your Linux OS version. For example, to download the veeam-ueficert package for SLES 15 SP7, navigate to the /backup/linux/agent-13/rpm/sles/SLE_15_SP7/noarch/ directory.
- Save the package to your computer.
- Install the veeam-ueficert package by using the following command:
rpm -i <...>/veeam-ueficert-13.0.1.203-1.rpm |
where <...> is the full path to the directory that contains the veeam-ueficert package.
Depending on the Linux distribution and version, after you install the veeam-ueficert package, the following will happen:
- [For all supported Linux distributions except RHEL 10, AlmaLinux 10, Rocky Linux 10 and Oracle Linux 10] The key is automatically imported into the enrollment request.
TIP |
After the package is installed, you can verify that the key enrollment is planned for the next reboot using the following command: mokutil -N. If the command output shows that the key enrollment is not planned, import the public key manually. |
- [For RHEL 10, AlmaLinux 10, Rocky Linux 10 and Orcale Linux 10] According to enhanced security standards of the operating system, the Veeam kernel module key is not automatically imported during installation of the veeam-ueficert package. After you install the veeam-ueficert package, you must import the key manually using the following command:
mokutil --import /etc/uefi/certs/veeam-ueficert |
During manual key import, you will be prompted to provide a one-time MOK password that you will use to enroll the key.
After you install the veeam-ueficert package and import the key, you can confirm the key enrollment.
Importing MOK for DKMS Kernel Module
Veeam does not provide the ueficert package for the DKMS module because it is not possible to sign such module automatically. Depending on the Linux distribution and version, you may have several options to make your system load the Veeam DKMS module properly — for more information, see Linux documentation.
If your system runs on Ubuntu 22.04 and later, Debian 12.0 and later, RHEL / Oracle Linux 8 and later, after you install Veeam kernel module using DKMS, a new Machine Owner Key is generated. Depending on the Linux distribution, perform the following steps to request enrollment of the key to your system's firmware:
- [Debian 12.0 and later, RHEL / Oracle Linux 8 and later] By default, the key is stored in the /var/lib/dkms/ directory. To import the key, run the following command:
mokutil --import /var/lib/dkms/mok.pub |
- [Ubuntu 22.04 and later] After you install the Veeam kernel module, the key is generated and imported into your system automatically. By default, the key is stored in the /var/lib/shim-signed/mok directory.
When the key is imported into the enrollment request, you will be prompted to enter a password that you will use to confirm the enrollment of the key during MOK management. After you set the password, you can confirm the key enrollment.
To enroll the Veeam or DKMS-generated key to the MOK list, do the following:
- Reboot the computer.
- During reboot, when prompted, press any key to perform MOK management.
IMPORTANT |
The prompt will time out in 10 seconds. If you don't press any key, the system will continue booting without enrolling the key. If you don't enroll the key at reboot, you will have to reconfigure the key by reinstalling the veeam-ueficert package and reboot again. |
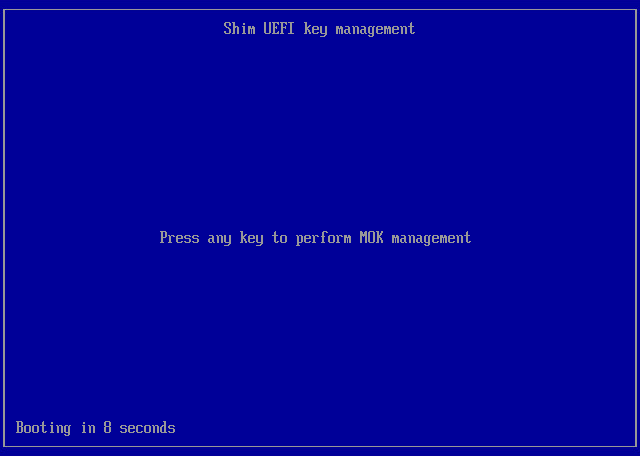
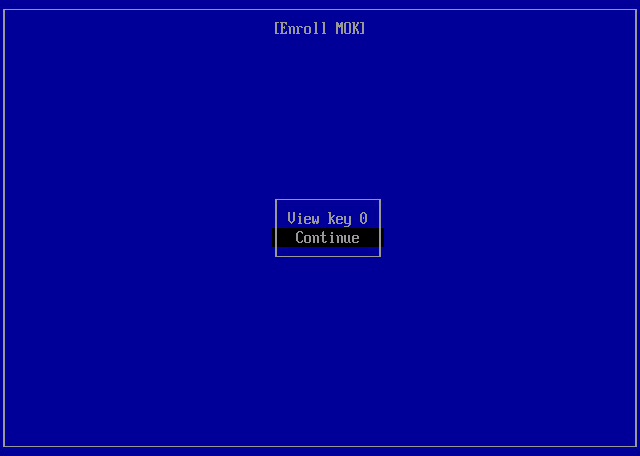
- At the first step of the wizard, select Enroll MOK and press [Enter].
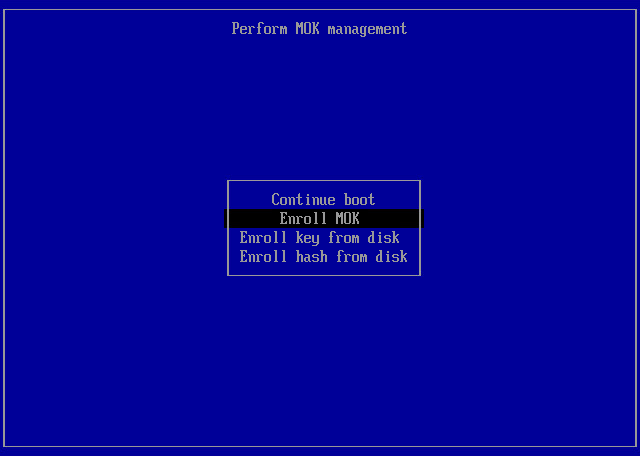
- At the Enroll MOK step, select Continue and press [Enter].
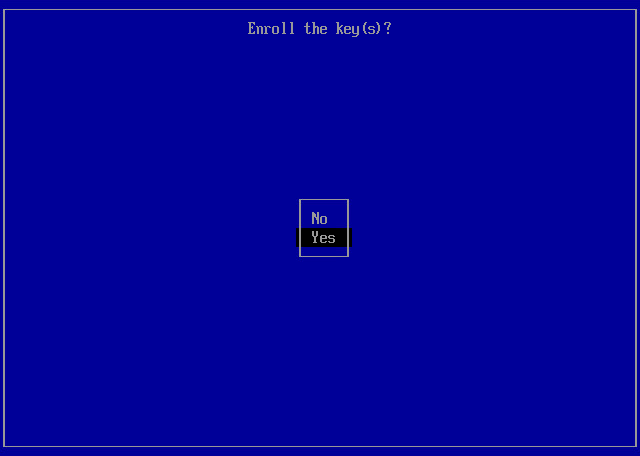
- At the Enroll the key(s) step, select Yes and press [Enter].
- Depending on whether the key was imported automatically or manually, do the following:
- If the key was imported automatically, type in the password for the root account and press [Enter].
- If the key was imported manually, type in the password you set when you imported the key and press [Enter].
- At the final step, select Reboot and press [Enter].
- After the system reboots, verify that the key is successfully enrolled with the following command: mokutil -l. The system will list the enrolled keys.