Configuring SSO for Microsoft Entra ID
To configure SSO authentication with Microsoft Entra ID:
- Log in to Veeam Service Provider Console.
For details, see Accessing Veeam Service Provider Console.
- At the top right corner of the Veeam Service Provider Console window, click Configuration.
- In the configuration menu on the left, click Roles & Users.
- On the Single Sign-On tab, click New and select Custom from the drop-down list.
The identity provider configuration wizard will open.
- Access the Microsoft Azure web portal.
- Navigate to the Enterprise Applications tab.
- In the menu on the left, select All applications.
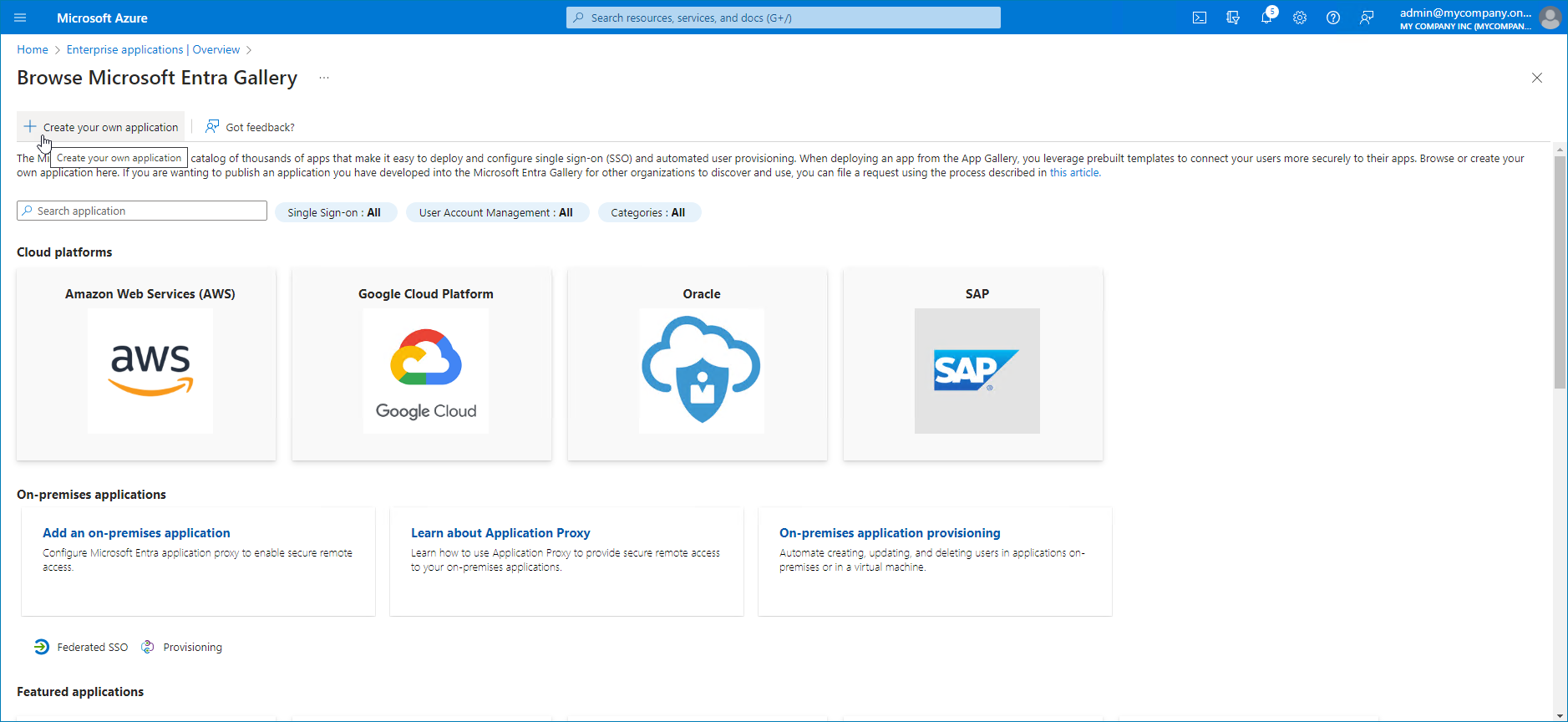
- At the top of the list, click New application.
- In the Browse Microsoft Entra Gallery window, click Create your own application.
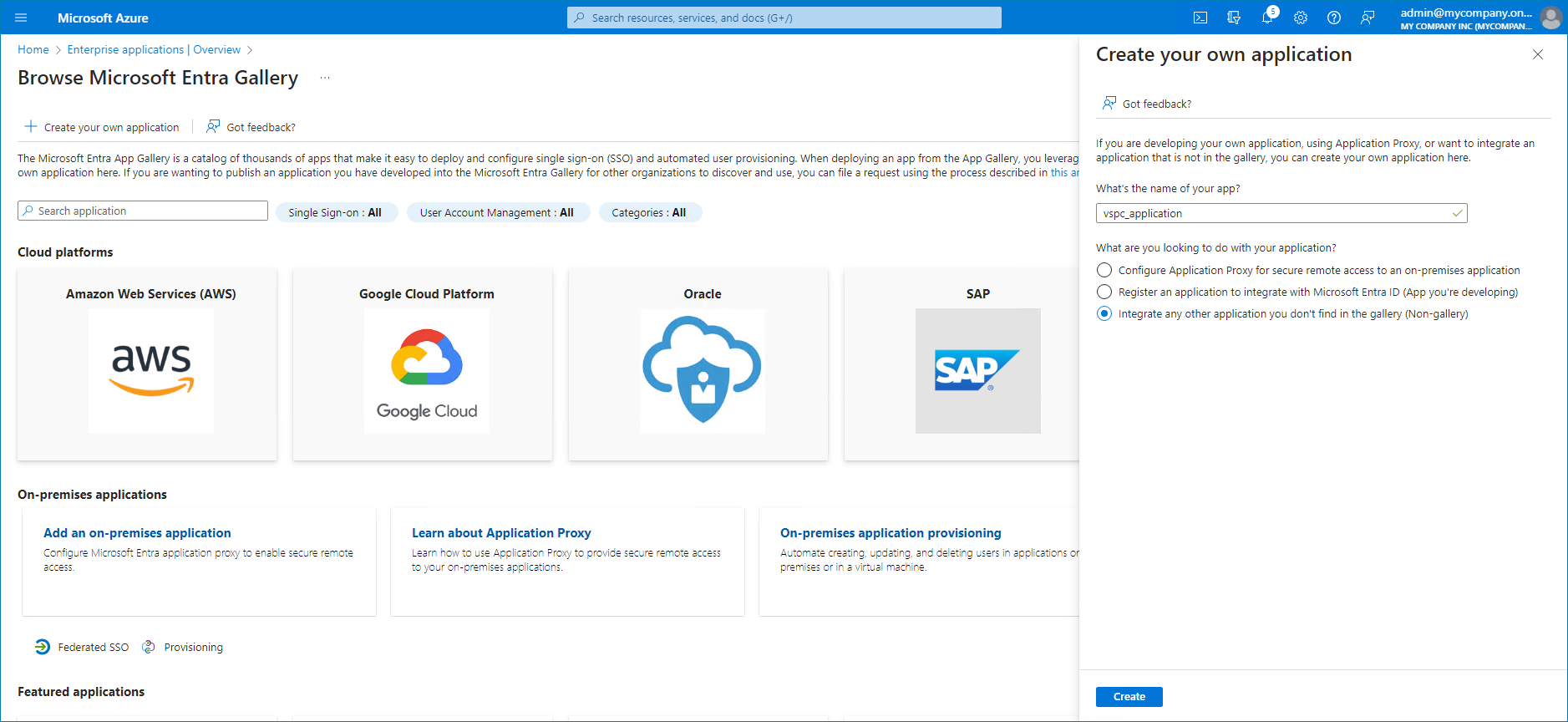
- In the Create your own application side window, specify the name of the integration with Veeam Service Provider Console and select Integrate any other application you don't find in the gallery (Non-gallery).
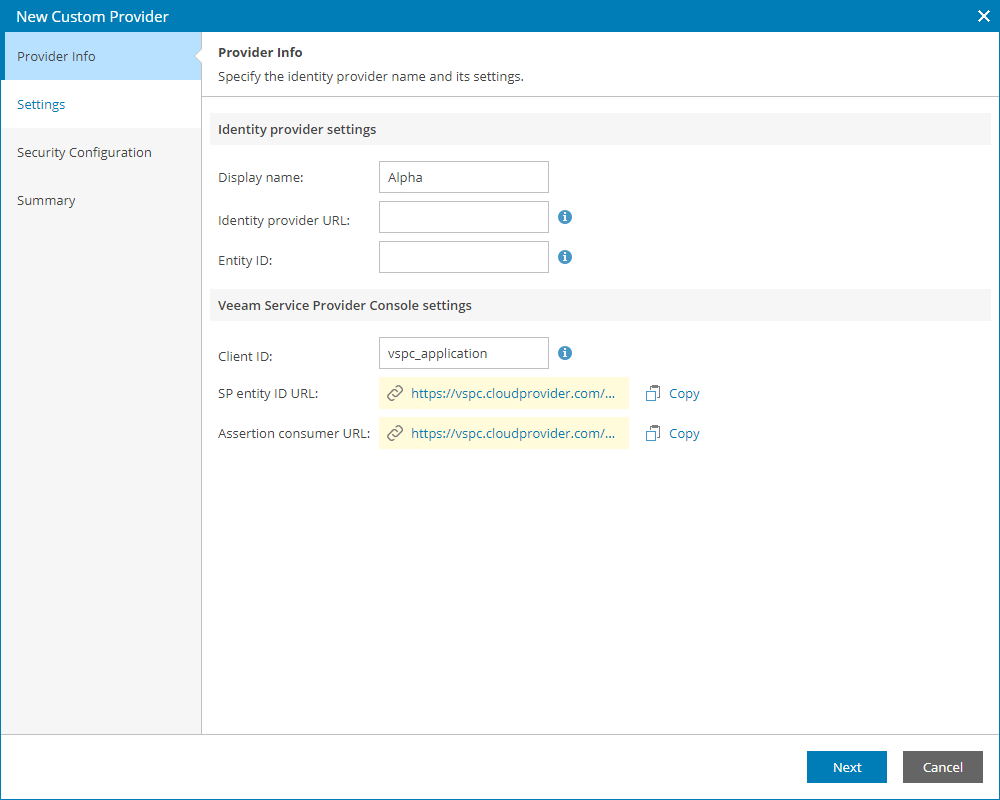
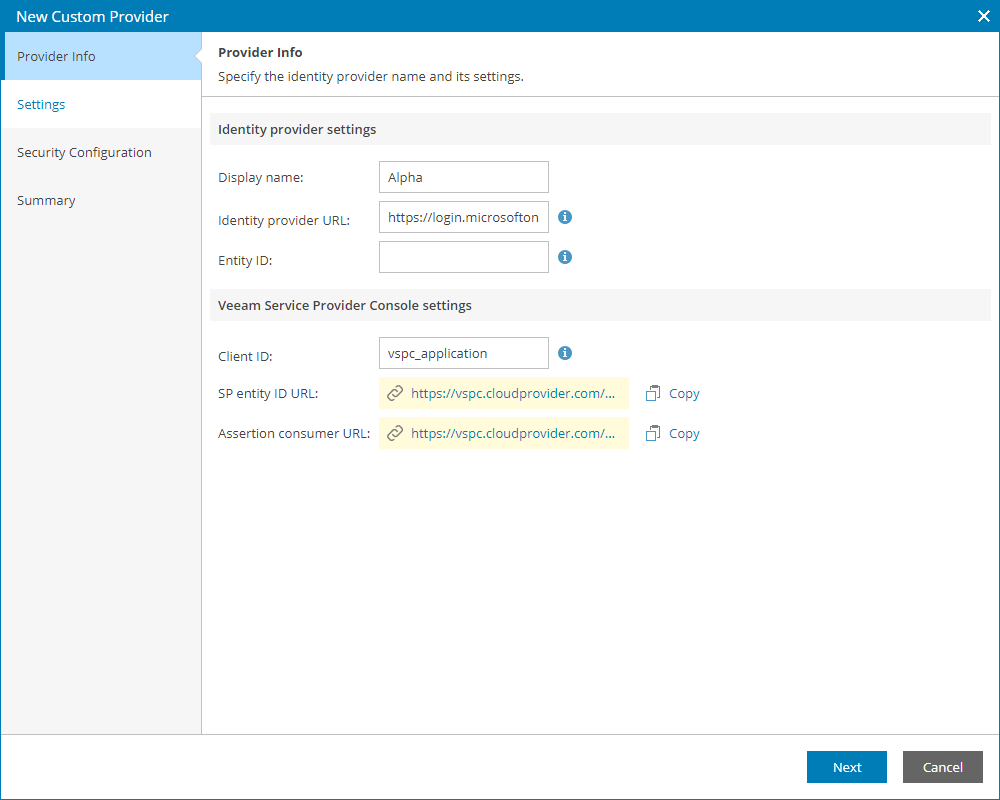
- In the Display name field, specify the IdP name that will be displayed in the IdP list on the Single Sign-On tab.
- In the Client ID field, insert the application name specified at step 10.
- Click Create SP entity ID link to generate entity ID URL based on the Client ID value.
Save the link locally.
If you apply changes to Client ID value after link generation, click New link.
- Click Create Assertion consumer link to generate assertion consumer service URL based on the Client ID value.
Save the link locally.
If you apply changes to Client ID value after link generation, click New link.
- In Microsoft Entra ID, open the created application.
- In the menu on the left, click Single sign-on and select SAML.
The SAML-based Sign-on page will open.
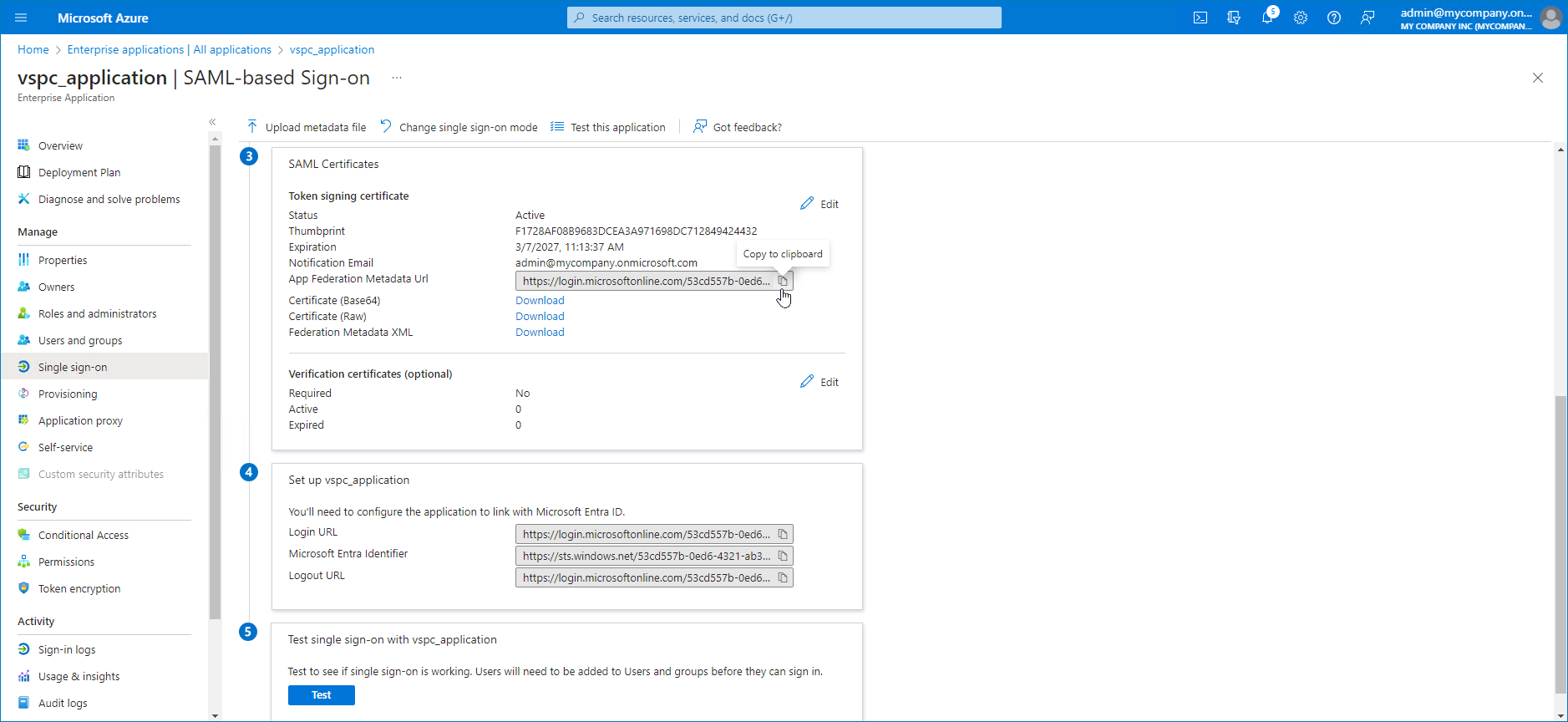
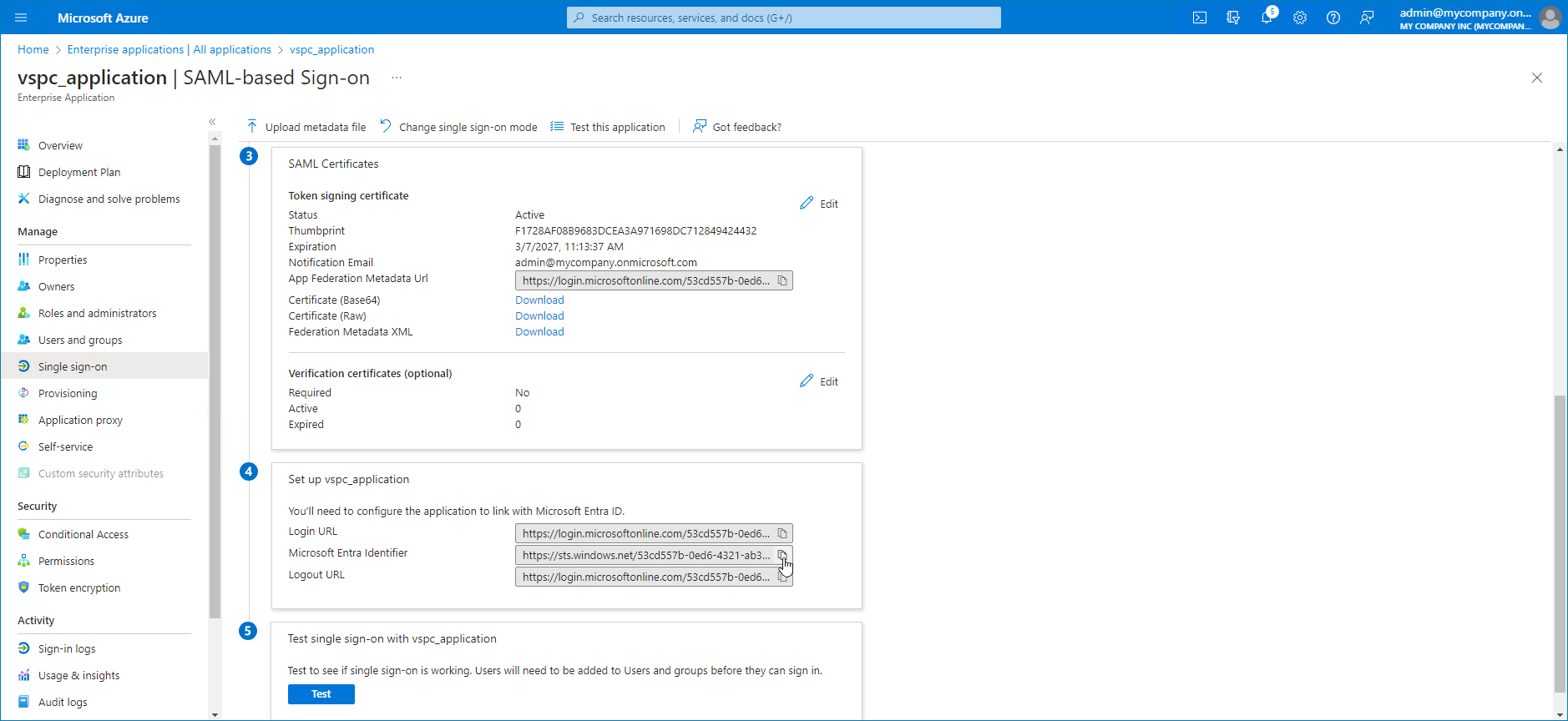
- Copy the App Federation Metadata URL link.
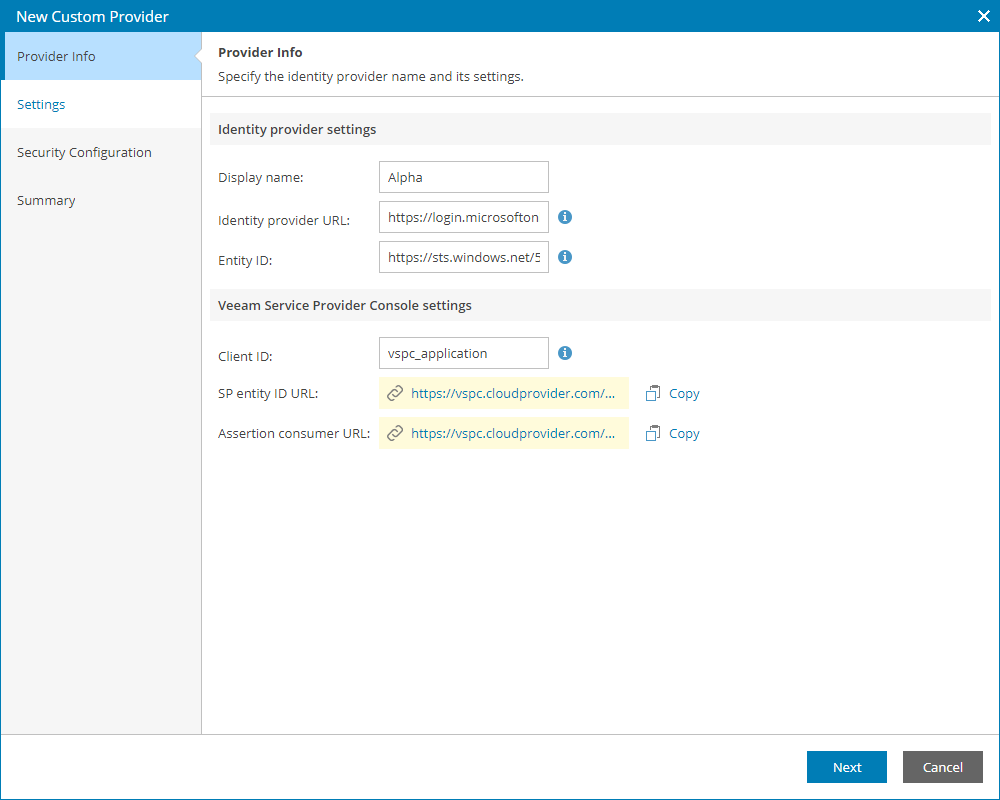
- In Veeam Service Provider Console, insert the URL into the Identity Provider URL field.
- In Microsoft Entra ID, from the Set up ... widget, copy the Microsoft Entra Identifier link.
- In Veeam Service Provider Console, paste the link into the Entity ID field.
- Follow steps 6-8 described in the Adding Identity Providers section.
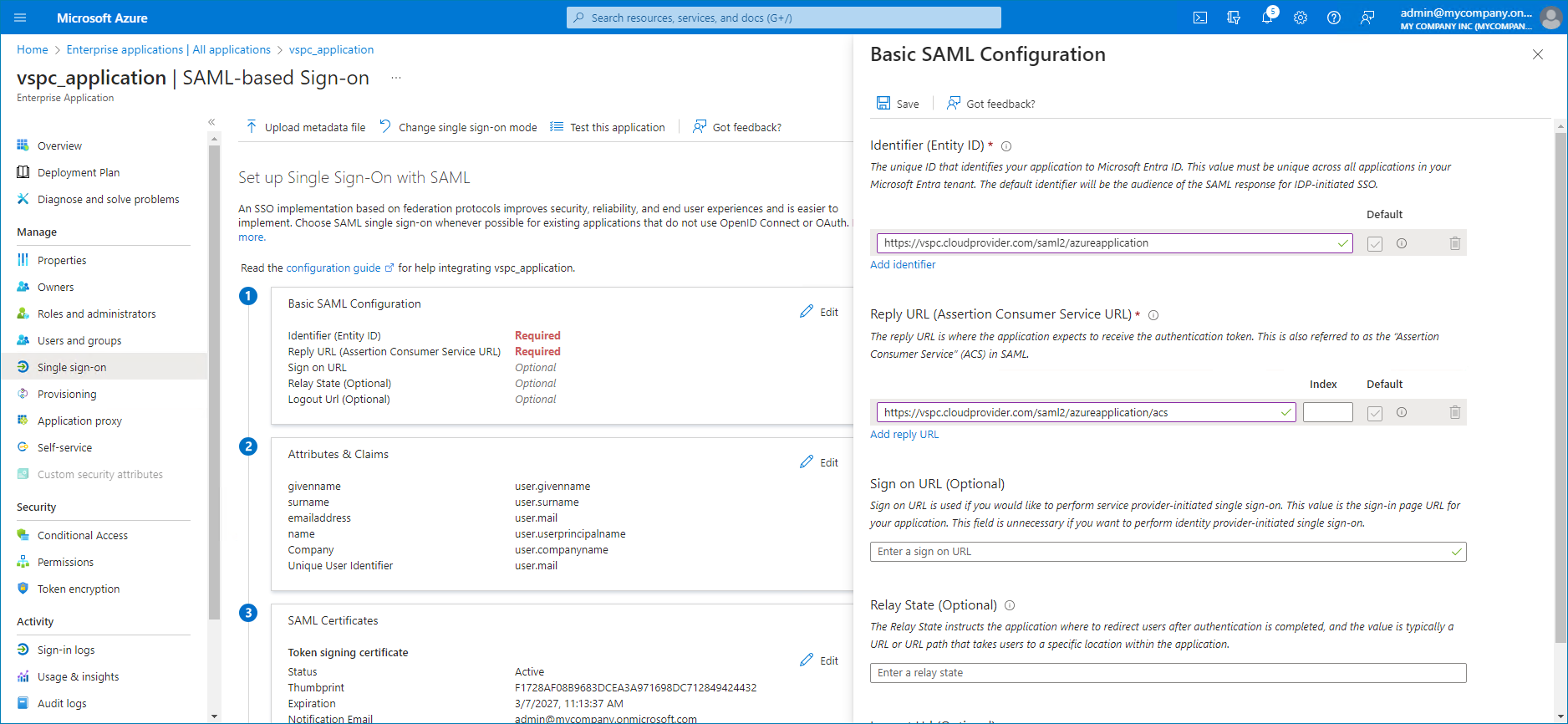
- In Microsoft Entra ID, in the top right corner of the Basic SAML Configuration widget, click Edit.
- In the Identifier (Entity ID) section, insert the URL generated in the SP entity ID URL field at step 11 into the empty field.
- In the Reply URL (Assertion Consumer URL) section, insert the URL generated in the Assertion consumer URL field at step 11 into the empty field.
- Click Save.
- In the top right corner of the Attributes & Claims widget, click Edit.
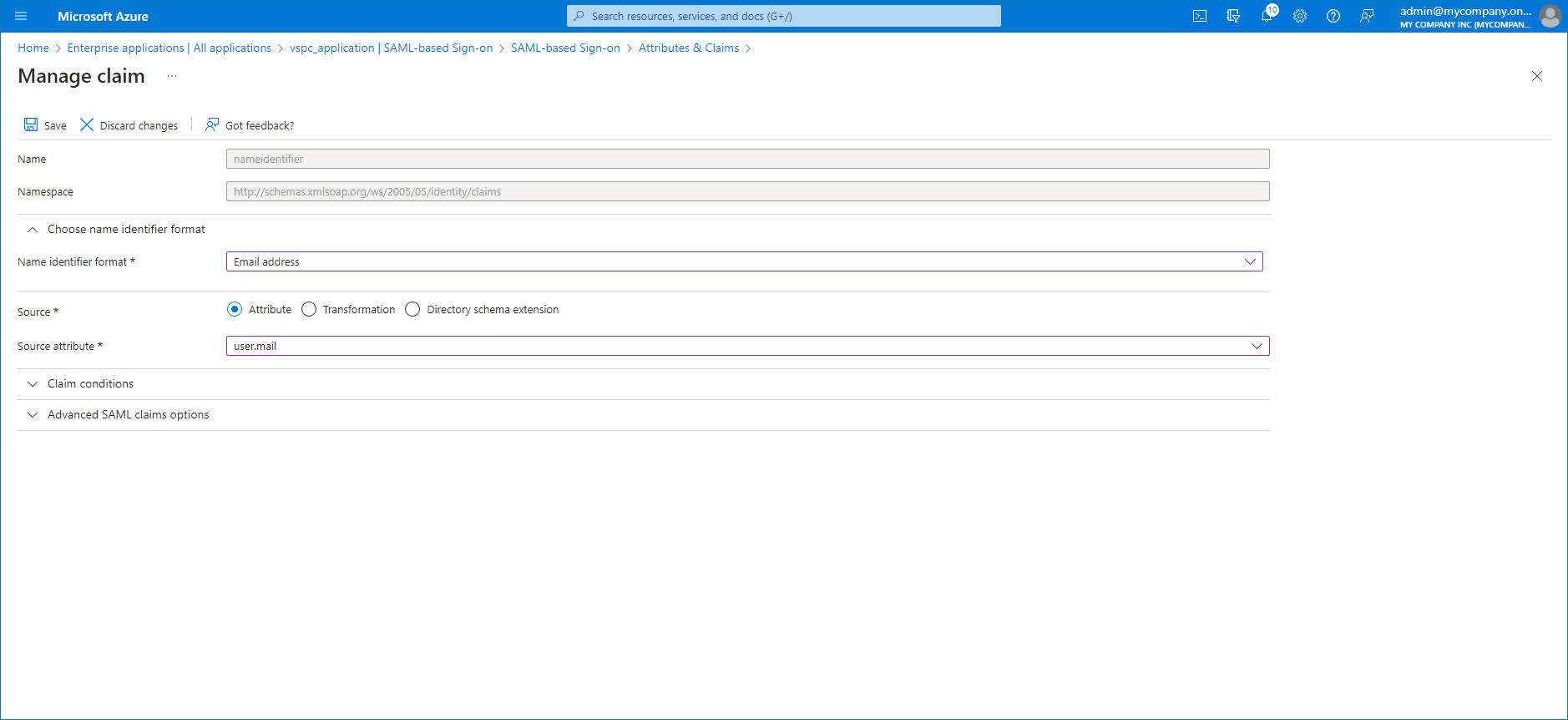
- Click the Unique User Identifier (Name ID) claim to modify claim settings.
- From the Source attribute list, select user.mail.
- Click Save.
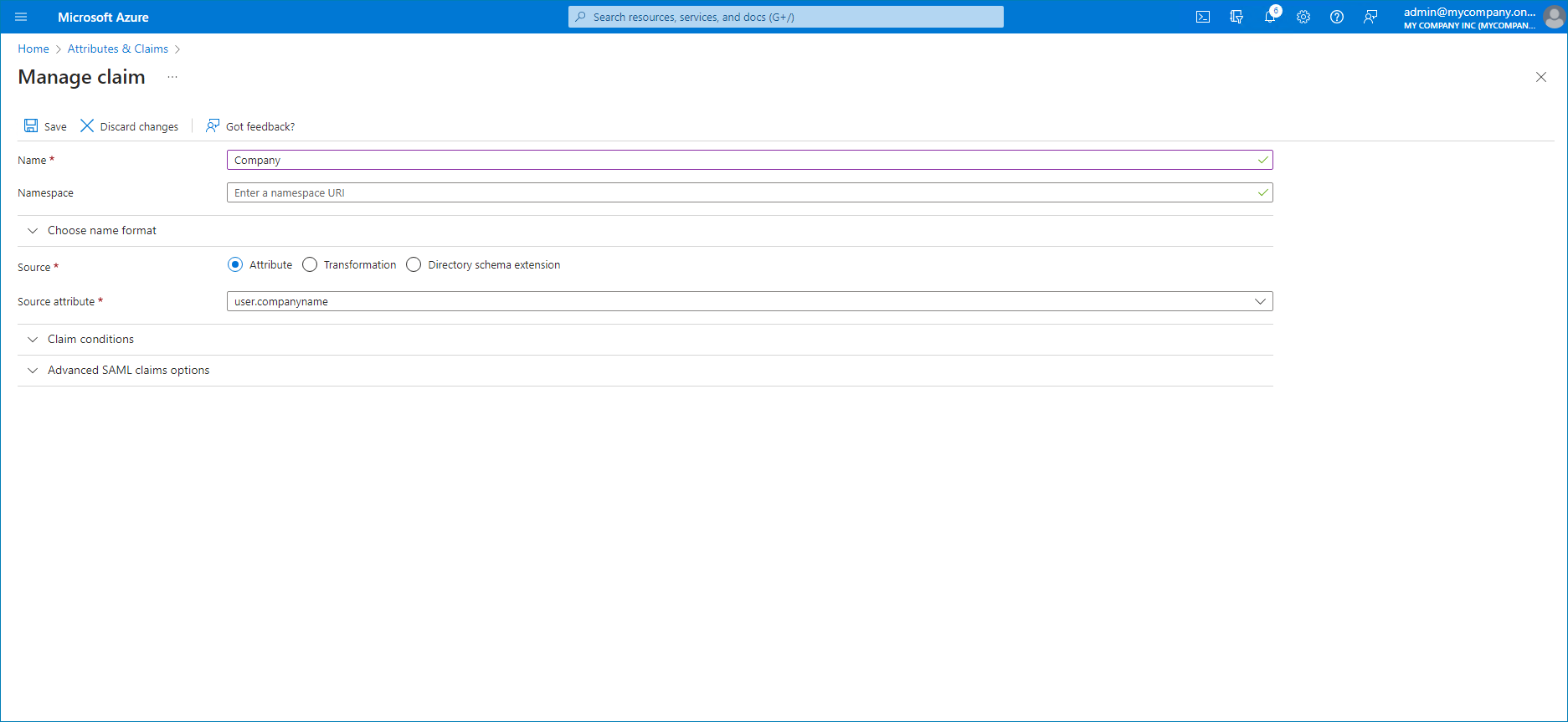
- At the top of the claims list, click Add new claim.
- In the Manage claim window, specify a claim name and from the Source attribute list, select user.companyname.
This claim will identify the company name specified in the user properties.
- Click Save.
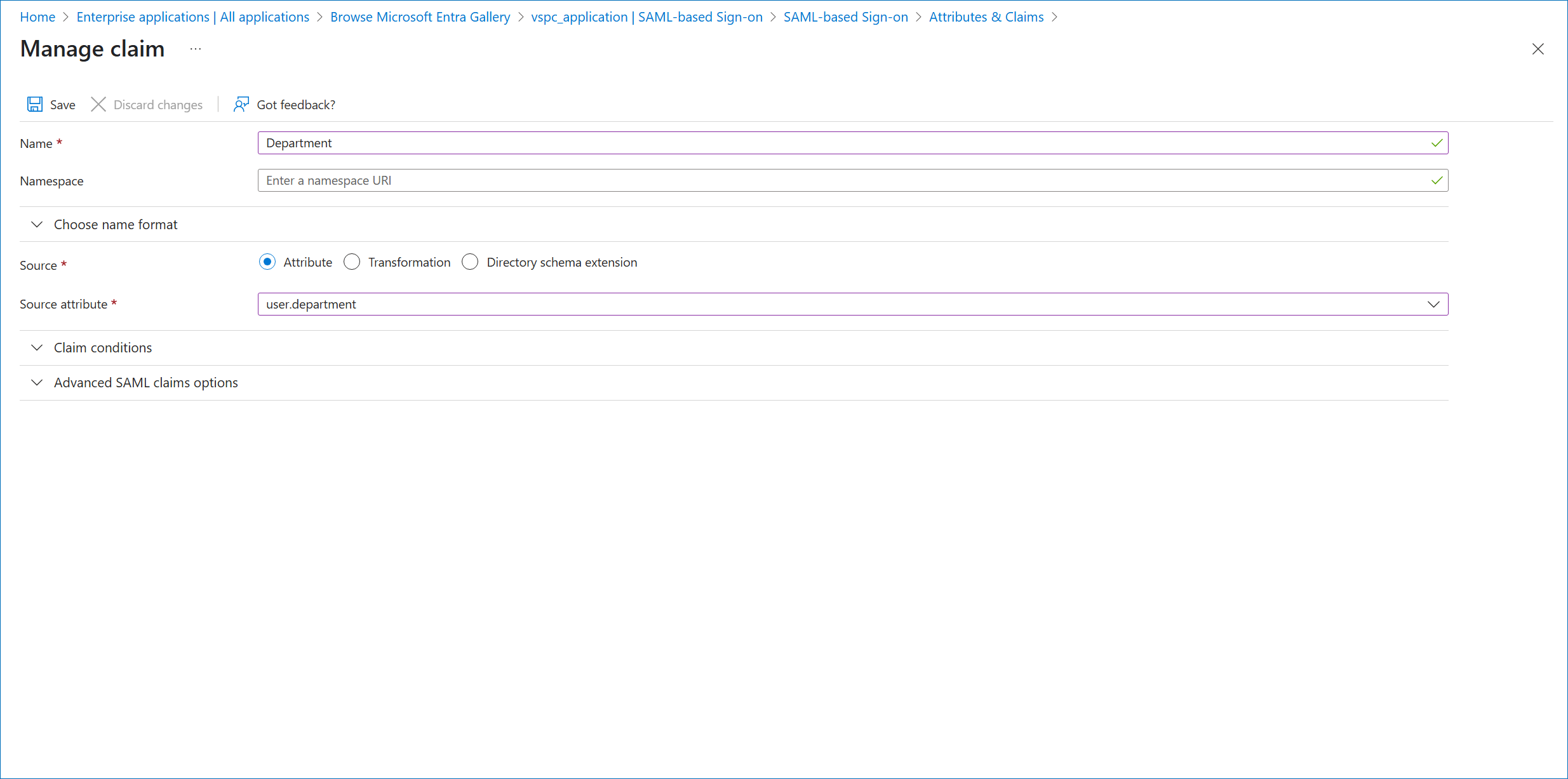
- If you want to add more claims, repeat steps 27–29 for all claims you want to add.
For example, you can add a claim to identify the department specified in the user properties.
- Close the Attributes & Claims window.
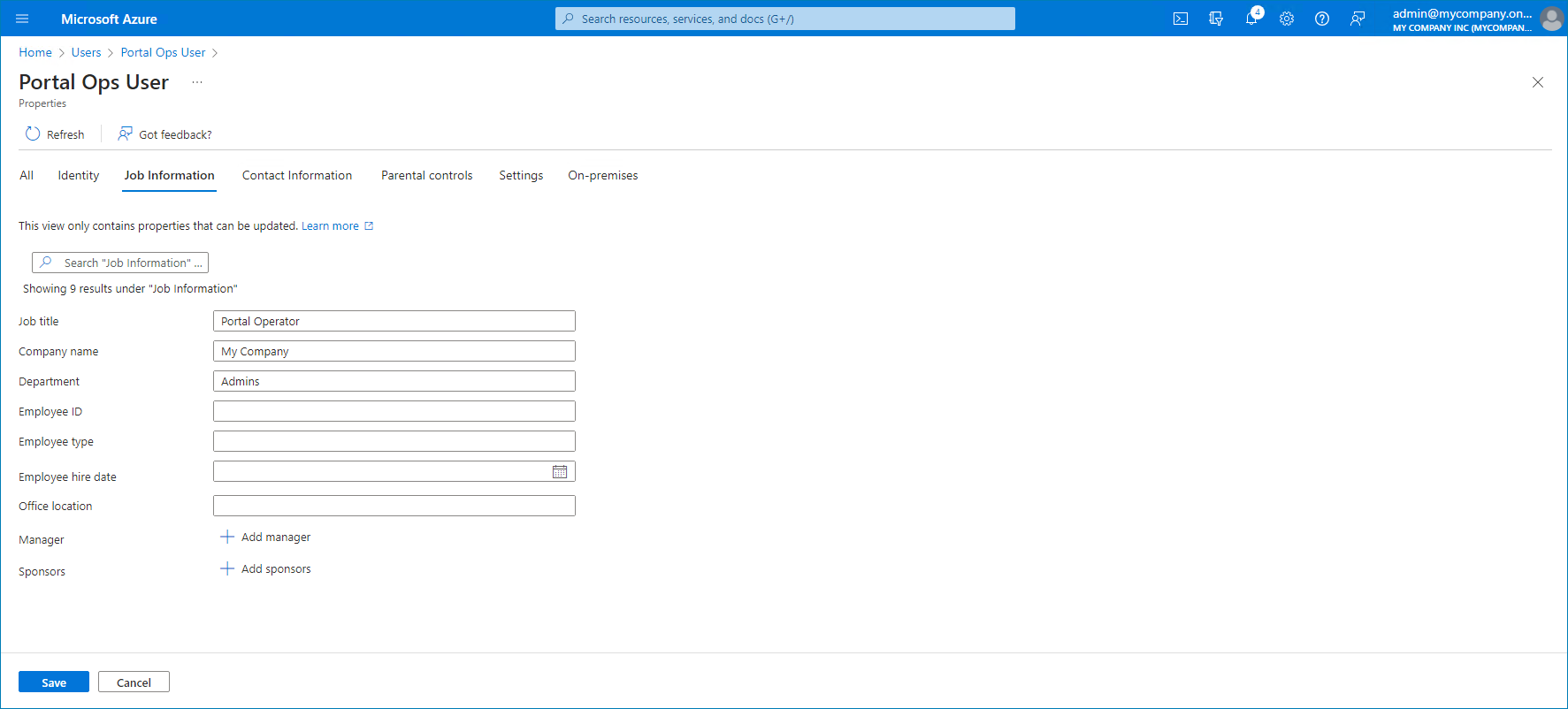
- Create users that you want to assign to the application.
Make sure to specify your Veeam Service Provider Console company name in the user properties.
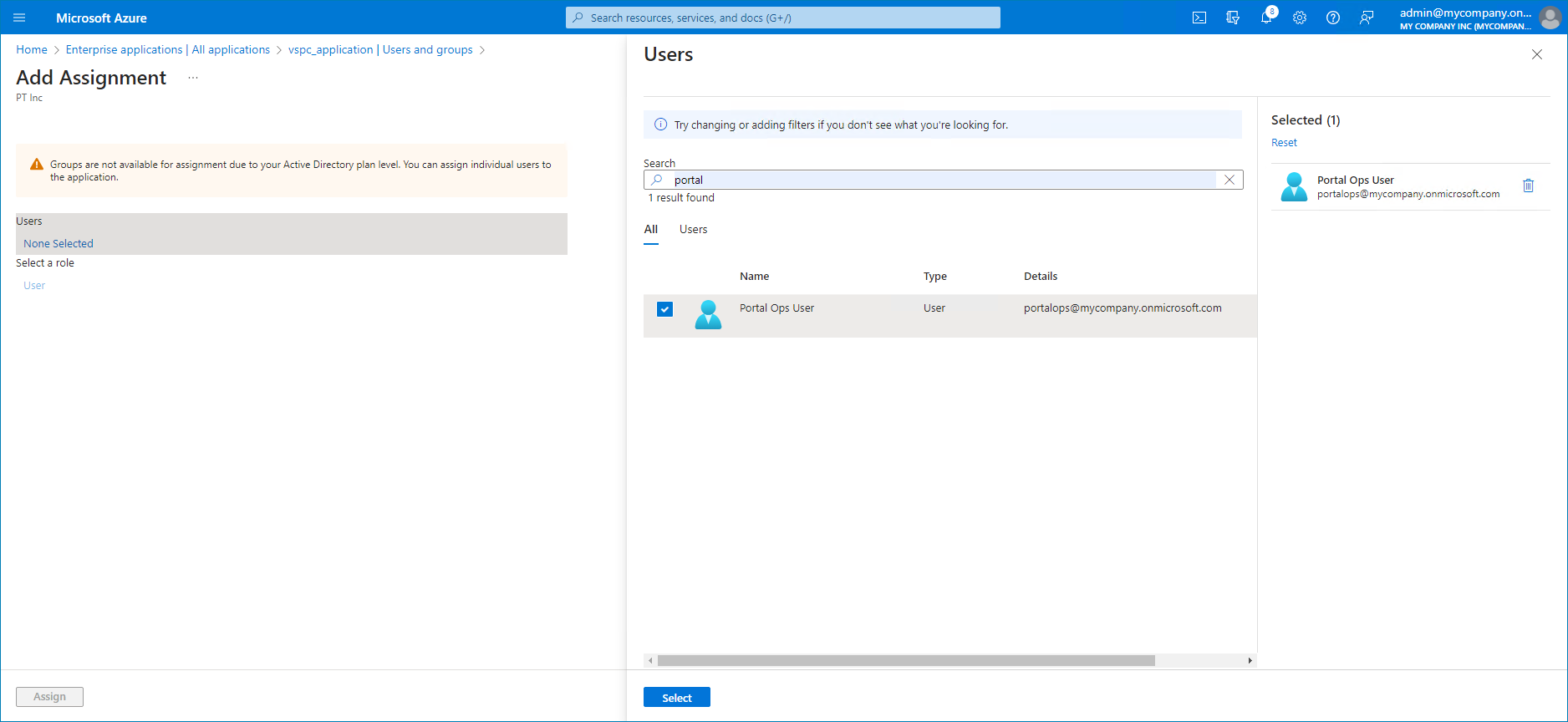
- In the menu on the left, select Users and Groups.
- At the top of the list, click Add user/group.
- In the Add Assignment window, click a link in the Users and groups section.
- Select the necessary user in the list and click Select.
- Click Assign.
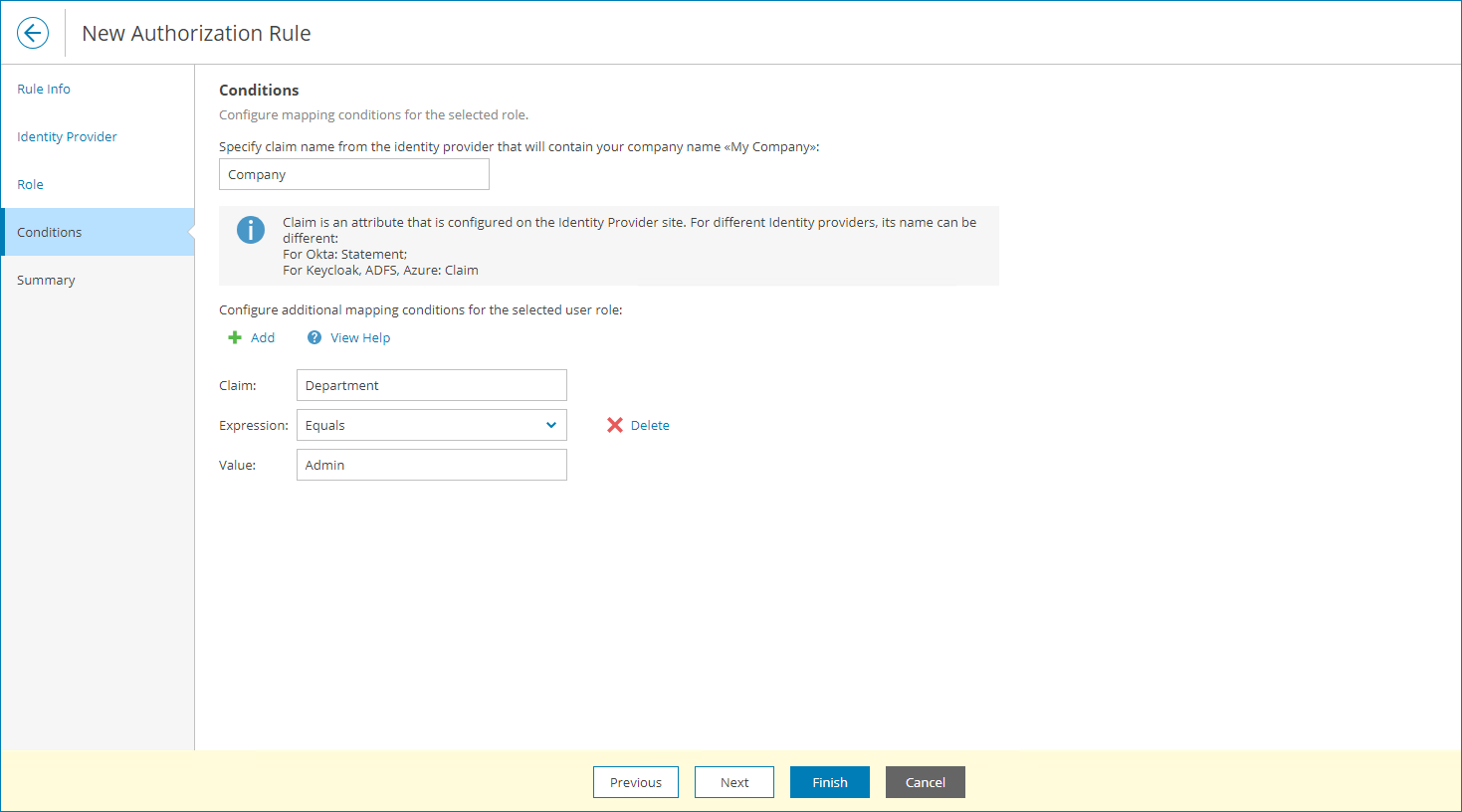
- In Veeam Service Provider Console, follow steps 1–8 of the New Authorization Rule wizard as described in Managing Mapping Rules section.
- At the Conditions step of the wizard, specify the claim name of the claim configured on step 28 and configure mapping conditions.
- Review the configured mapping rule and click Finish.
- In the configuration menu on the left, click Security and open the Single Sign-On tab.
- From the Configuration drop-down list, select Test Login.
Veeam Service Provider Console will complete the identity provider configuration and perform a trial authorization.