This is an archive version of the document. To get the most up-to-date information, see the current version.
This is an archive version of the document. To get the most up-to-date information, see the current version.Step 6. Choose Capacity Type and Enable Encryption
[This step applies only if you have selected the Restore to a new location, or with different settings option at the Restore Mode step of the wizard]
At the Cluster Capacity step of the wizard, you can configure capacity and encryption settings for the restored Aurora DB cluster:
Important |
Before configuring capacity settings, check the limitations and prerequisites described in section Limitations and Considerations. |
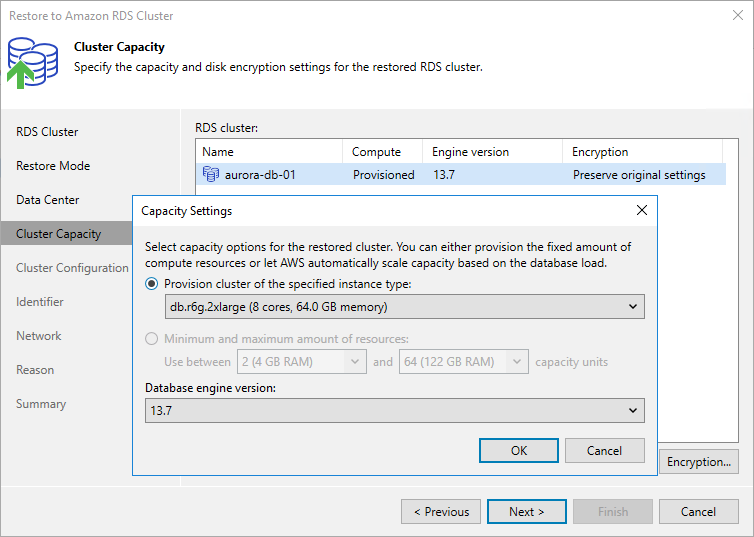
- Click Capacity. Then, in the Capacity Settings window:
- From the Provision cluster of the specified instance type drop-down list, select a DB instance class that will be used to create the primary DB instance in the restored cluster. For a DB instance class to be displayed in the list, it must be supported for the Aurora DB engine of the source Aurora DB cluster. For more information on supported DB instance classes, see AWS Documentation.
If you want to restore the primary DB instance of the provisioned cluster as an Aurora Serverless v2 DB instance, select db.serverless from the drop-down list. Consider that Aurora Serverless v2 is supported only for a limited list of DB engine versions. For more information, see AWS Documentation.
- [Applies only to Aurora Serverless v2] Use the Min capacity and Max capacity fields to specify a range of capacity units that will be used to create scaling rules for the restored cluster. These rules define thresholds for CPU utilization, connections and available memory.
For more information on capacity units and scaling rules, see AWS Documentation.
- From the Database engine version drop-down list, select an Aurora database engine version for the restored cluster. The list shows only DB engine versions supported in the target AWS Region, and is filtered based on the DB engine type and DB engine version of the source Aurora DB cluster.
For more information on Amazon Aurora database engine versions, see AWS Documentation.
Important |
For more information on Aurora MySQL parallel query, see AWS Documentation. |
- Click Encryption. Then, in the Disk encryption window:
- Select the Preserve the original encryption settings option if you do not want to encrypt the restored cluster or want to apply the original encryption scheme of the source cluster.
If you plan to restore an unencrypted provisioned DB cluster to Aurora Serverless and want to preserve the original encryption settings, note that the backup appliance will encrypt the newly created Aurora Serverless DB cluster with the default KMS key in the target AWS Region. For more information on Aurora Serverless, see AWS Documentation.
- Select the Use the following encryption password option if you want to encrypt the restored cluster with an AWS KMS key. Then, choose the necessary KMS key from the list.
For a KMS key to be displayed in the list of available encryption keys, it must be stored in AWS Region select at step 5 of the wizard, and the IAM role specified for the restore operation must have permissions to access the key. For more information on KMS keys, see AWS Documentation.
Tip |
If the necessary KMS key is not displayed in the list, or if you want to use a KMS key from an AWS account other than the AWS account to which the specified IAM role belongs, you can specify the amazon resource number (ARN) of the key in the Use the following encryption key field. For Veeam Backup & Replication to be able to encrypt the restored Aurora DB cluster using the provided KMS key, either the IAM role or user specified for the restore operation, or the IAM role used to create the restore point selected at step 2 of the wizard must have permissions to access the key. |