Enabling Automatic Protection
To instruct Veeam Backup for AWS to protect VPC configuration of all AWS Regions specified in EC2, RDS, DynamoDB, Redshift Clusters, Redshift Serverless, EFS and FSx backup policy settings, in the Automatically protected regions section, set the Automatically collect VPC settings toggle to On. To retrieve VPC configurations of all automatically protected AWS Regions, Veeam Backup for AWS will use the permissions of IAM roles specified either in the organization settings (if you back up resources within an AWS Organization), or in the backup policy settings (if you back up resources belonging to a single AWS account).
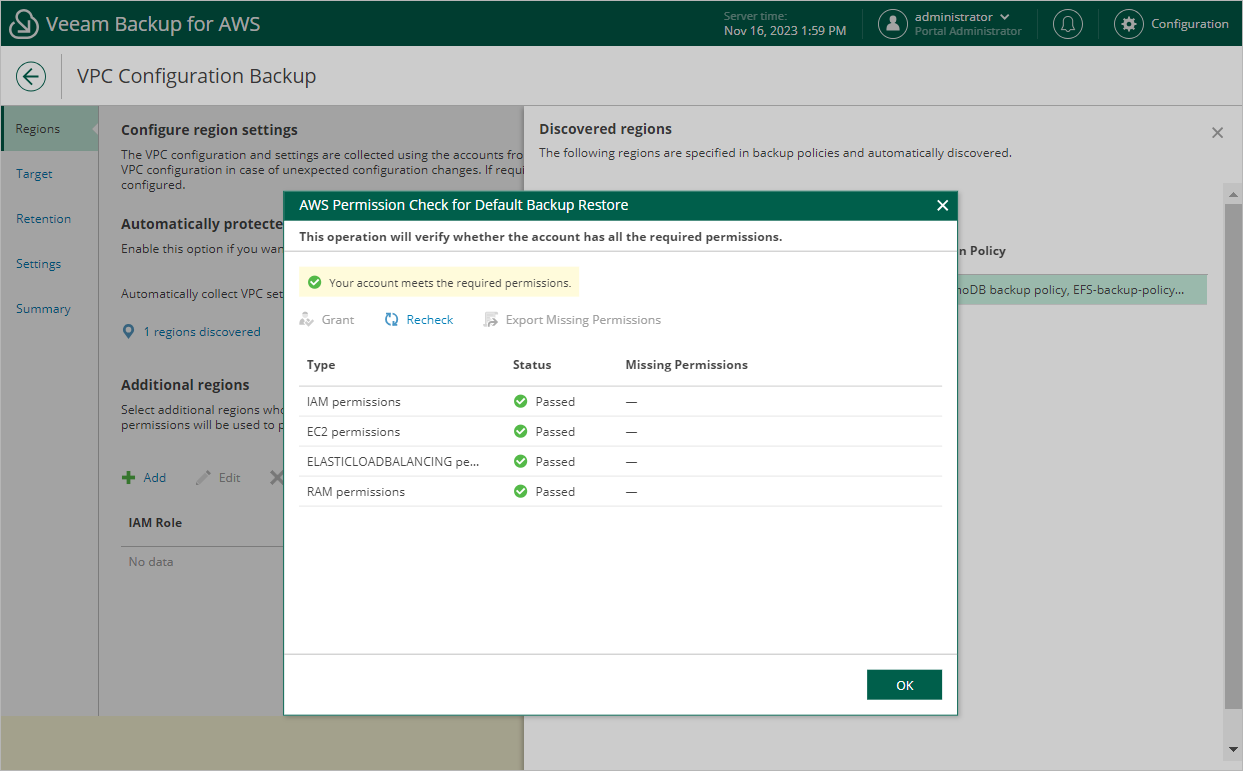
It is recommended that you check whether IAM roles specified in the backup policy settings have all the permissions required to perform Amazon VPC configuration backup. If some permissions of the IAM role are missing, the backup policy will fail. To run the IAM role permission check, do the following:
- In the Automatically Protected Regions section, click the Discovered regions link.
- In the Discovered regions window, select the IAM role whose permissions you want to check.
- Click Check Permissions.
Veeam Backup for AWS will display the AWS Permission Check window where you can view the progress and results of the performed check. If some permissions of the IAM role are missing, the check will complete with errors. You can view the list of permissions that must be granted to IAM roles in the Missing Permissions column. For more information on the required permissions, see VPC Configuration Backup IAM Role Permissions.
You can grant the missing permissions to IAM roles in the AWS Management Console or instruct Veeam Backup for AWS to do it. To learn how to grant permissions to IAM roles using the AWS Management Console, see AWS Documentation. To let Veeam Backup for AWS grant the missing permissions:
- In the AWS Permission Check window, click Grant.
- In the Grant Permissions Window, provide one-time access keys of an IAM user that is authorized to update permissions of the IAM role, and then click Apply.
The IAM user whose access keys are used to update the IAM role must have the following permissions:
"iam:AttachRolePolicy", "iam:CreatePolicy", "iam:CreatePolicyVersion", "iam:CreateRole", "iam:GetAccountSummary", "iam:GetPolicy", "iam:GetPolicyVersion", "iam:GetRole", "iam:ListAttachedRolePolicies", "iam:ListPolicyVersions", "iam:SimulatePrincipalPolicy", "iam:UpdateAssumeRolePolicy" |
Important |
|