Worker Instances in Private Environment
Veeam Backup for AWS automatically deploys worker instances in Amazon EC2 for the duration of backup, restore and retention processes and removes it immediately after the processes complete. Veeam Backup for AWS deploys one worker instance per each processed AWS resource. To minimize cross-region traffic charges, depending on the data protection or disaster recovery operation, Veeam Backup for AWS deploys the worker instance in specific locations.
Important |
If you want worker instances to operate in a private network, consider that worker instances must have outbound access to specific AWS services. |
By default, Veeam Backup for AWS uses public access to communicate with worker instances. However, you can instruct Veeam Backup for AWS to deploy worker instances without public IPv4 addresses, and then configure worker settings to allow private network access. One possible solution is to enable the private network deployment functionality in the Veeam Backup for AWS Web UI, create interface endpoints and ensure connectivity between your resources:
- Set the Private network deployment toggle to On as described in section Configuring Private Network Deployment.
- To allow worker instances to access AWS services, create specific VPC interface endpoints for all subnets to which the worker instances will be connected.
For the list of VPC interface endpoints required for backup and restore operations, see Configuring Private Networks.
- To enable route traffic between different VPCs, create peering connections between those VPCs.
- To enable private traffic between different VPCs, add routes to the route tables associated with the subnets of those VPCs.
- To allow Veeam Backup for AWS to deploy worker instances based on VPC networks and subnets for which you have created VPC interface endpoints, add the necessary worker configurations as described in section Managing Worker Configurations.
If you do not add specific worker configurations, Veeam Backup for AWS will use either the default or the most appropriate network settings of AWS Regions.
The actions you perform depend on specific use cases. For more information, see Example 1. Creating EC2 Backups and Example 2. Archiving EC2 Backups.
Important |
If you enable the private network deployment functionality, consider the following:
|
Requirements for Private Network Deployment
If you enable the private network deployment functionality, consider the following:
- The backup appliance and worker instances must be able to communicate with the Amazon S3 service through an S3 interface endpoint. That is why security groups associated with the endpoint network interface must allow inbound HTTPS traffic from both the backup appliance and the worker instances through port 443.
- Specific VPC interface endpoints must be created for subnets to which worker instances will be connected to access AWS services, and the security group associated with the endpoint network interfaces must allow local inbound traffic through port 443.
For the list of VPC interface endpoints required for specific backup and restore operations, see Configuring Private Networks.
- Security groups associated with the worker instances must allow outbound HTTPS traffic to all endpoints through port 443.
Important |
S3 gateway endpoints are not supported when using the private network deployment functionality. |
Example 1. Creating EC2 Backups
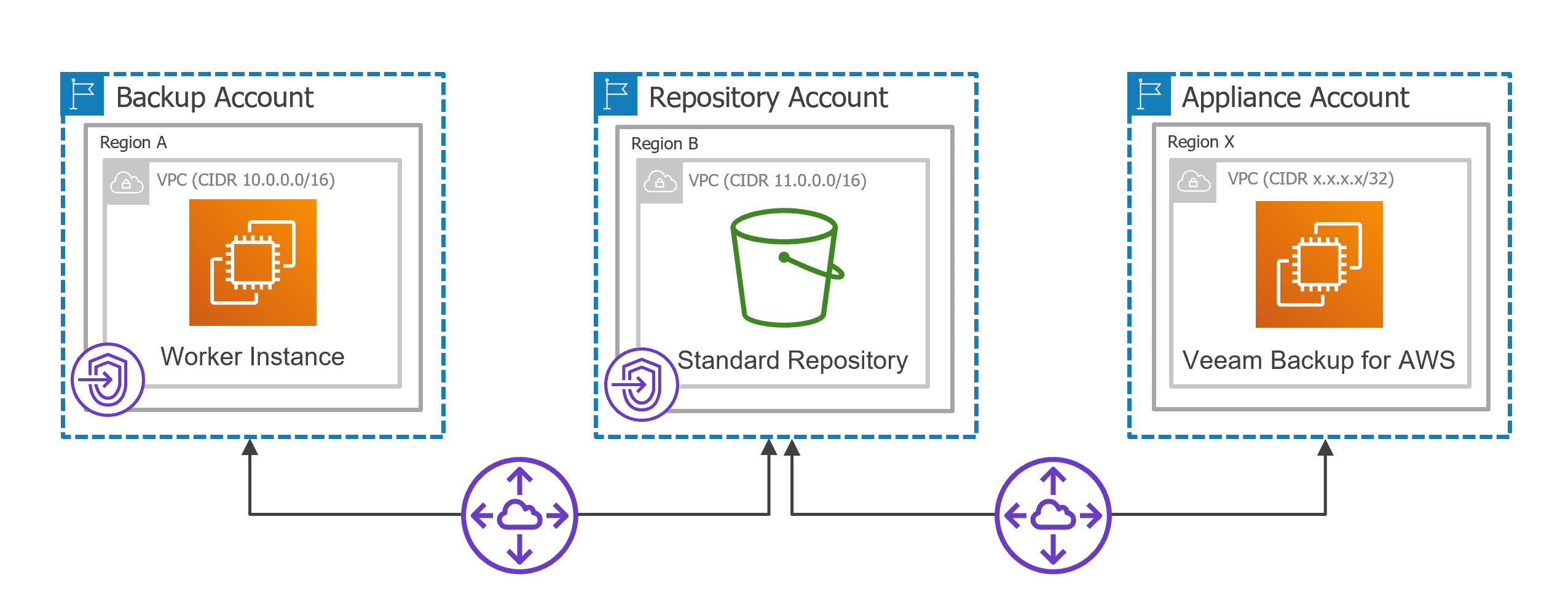
Consider the following example. You need to back up an EC2 instance that belongs to a production account located in region A by deploying a worker instance in a backup account located in the same region and store its image-level backups in a backup repository that belongs to a repository account located in region B. The backup appliance belongs to an appliance account located in region X.
Note |
To perform EC2 backup, Veeam Backup for AWS by default deploys worker instances in the backup account in the same AWS Region where source EC2 instances reside. However, you can instruct Veeam Backup for AWS to deploy worker instances in a production account. For more information, see Worker Deployment Options. |
In this case, you can perform the following steps in the AWS Management Console.
- Establish a connection between the backup account and the repository account. To do that:
- Create interface VPC endpoints required for worker instances to access AWS services.
- Create a VPC to which the worker instances will be connected (for example, 10.0.0.0/16) and a private subnet in the backup account. Note that the Enable DNS name check box must be enabled in the VPC settings.
- Create interface VPC endpoints for the private subnet to which the worker instances will be connected. These endpoints will be used to access the ssm, sqs, ebs, ec2messages services.
- Create security groups associated with the endpoint network interfaces to allow local inbound HTTPS traffic (port 443).
It is recommended that you specify the full IPv4 address range of the VPC in the security group settings to make the created interface endpoints available for all resources in the VPC. If a security group restricts inbound HTTPS traffic from the resources, you will not be able to send traffic through the endpoint network interfaces.
- Configure an S3 interface endpoint required for the worker instances to access the Amazon S3 service.
- Create a VPC (for example, 11.0.0.0/16) and a private subnet in the repository account. Make sure that the CIDR block of the repository VPC differs from the CIDR block of the worker instance VPC to avoid subnet CIDR block conflicts.
- Create an S3 interface VPC endpoint for the private subnet to which the worker instances will be connected. The endpoint will be used to access the Amazon S3 service.
- Create a security group associated with the endpoint network interface to allow inbound HTTPS traffic (port 443) from both the backup appliance and the worker instances.
Security Group | From | Protocol | Port | Notes |
|---|---|---|---|---|
Group associated with the VPC interface endpoints | Worker instance VPC (10.0.0.0/16) | TCP | 443 | Allows local inbound HTTPS traffic |
Group associated with the S3 interface endpoint | Appliance VPC (x.x.x.x/32) | TCP | 443 | Allows inbound HTTPS traffic from the backup appliance |
Worker instance VPC (10.0.0.0/16) | TCP | 443 | Allows inbound HTTPS traffic from the worker instances |
- Configure the following peering connection settings.
- Create a VPC peering connection between the worker instance VPC and repository VPC, and accept the peering request to enable route traffic between those VPCs.
- Add routes to the route tables associated with the subnets of the worker instance VPC and repository VPC to enable private traffic between those VPCs.
Destination | Target |
|---|---|
Worker Instance VPC | |
Worker instance VPC (10.0.0.0/16) | Local |
Repository VPC (11.0.0.0/16) | pcx-xxxx |
Repository VPC | |
Repository VPC (11.0.0.0/16) | Local |
Worker instance VPC (10.0.0.0/16) | pcx-xxxx |
- Establish a connection between the repository account and the appliance account. To do that:
- Create a VPC peering connection between the appliance VPC and repository VPC, and accept the peering request to enable route traffic between those VPCs.
- Add routes to the route tables of the repository VPC and appliance VPC to enable private traffic between those VPCs.
Destination | Target |
|---|---|
Repository VPC | |
Repository VPC (11.0.0.0/16) | Local |
Worker instance VPC (10.0.0.0/16) | pcx-xxxx |
Appliance VPC (x.x.x.x/32) | pcx-yyyy |
Appliance VPC | |
Appliance VPC (x.x.x.x/32) | Local |
Repository VPC (11.0.0.0/16) | pcx-yyyy |
For detailed instructions on how to create interface endpoints, set up VPC peering connections and add routing, see Configuring Private Networks.
Tip |
If you have multiple AWS accounts and want to deploy worker instances in production accounts, you can create a single resource share in one AWS account for all subnets to which the worker instances will be connected. The resource share can be further used to share these subnets with other AWS accounts in any organization. For more information, see Configuring Private Networks for Production Accounts. |
Example 2. Archiving EC2 Backups
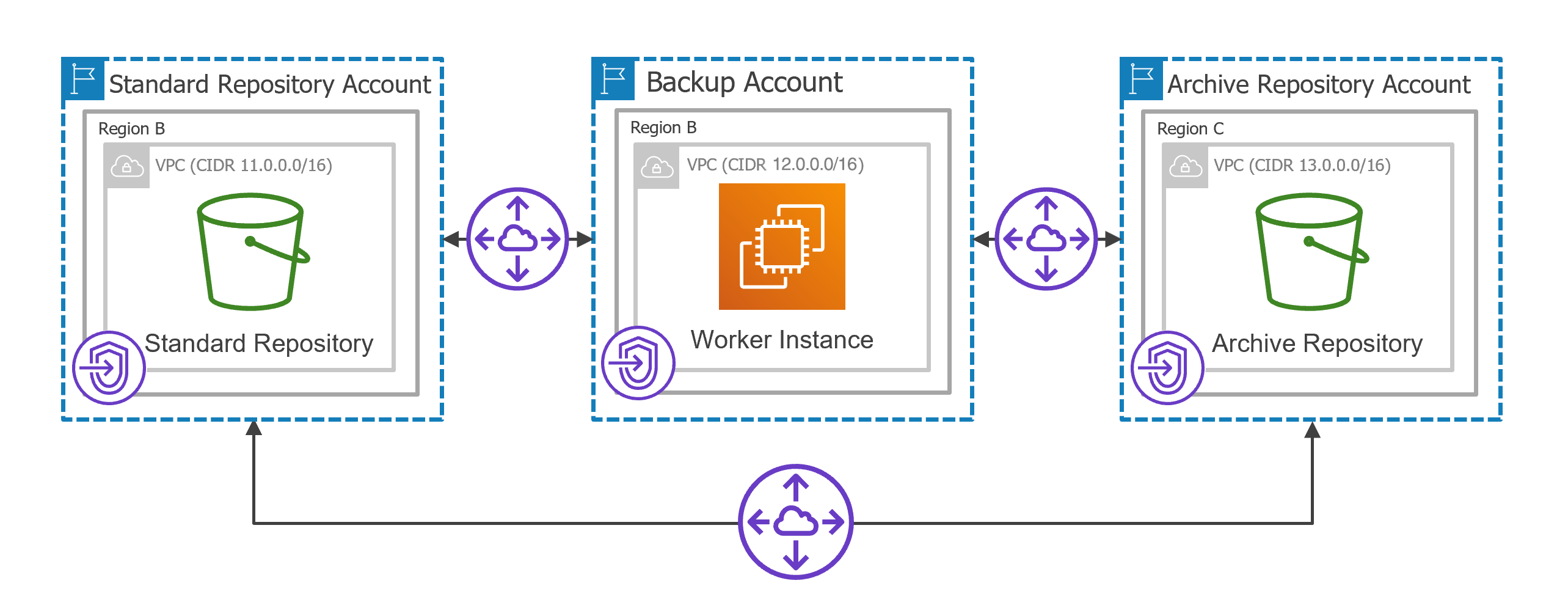
Consider the following example. You need to copy backed-up data stored in a standard backup repository that belongs to a repository account located in region B to an archive backup repository that belongs to a repository account located in region C.
Note |
To archive EC2 backups, Veeam Backup for AWS deploys worker instances in the backup account in the same AWS Region in which the standard backup repository with backed-up data resides. |
In this case, you can perform the following steps in AWS Management Console.
- Establish a connection between the backup account and the standard repository account. To do that:
- Create interface VPC endpoints required for worker instances to access AWS services:
- Create a VPC to which the worker instances will be connected (for example, 12.0.0.0/16) and a private subnet in the backup account.
- Create interface VPC endpoints for the private subnet to which the worker instances will be connected. These endpoints will be used to access the ssm, sqs and ec2messages services.
- Create security groups associated with the endpoint network interfaces to allow local inbound HTTPS traffic (port 443).
It is recommended that you specify the full IPv4 address range of the VPC in the security group settings to make the created interface endpoints available for all resources in the VPC. If a security group restricts inbound HTTPS traffic from the resources, you will not be able to send traffic through the endpoint network interfaces.
- Make sure that you have already configured the S3 interface endpoint in the standard repository account required for the worker instances to access the Amazon S3 service, as described in Example 1.
Important |
The backup appliance and worker instances must be able to communicate with the Amazon S3 service through the created S3 interface endpoint. That is why security groups associated with the endpoint network interface must allow inbound HTTPS traffic from both the backup appliance and the worker instances through port 443. |
- Configure the following peering connection settings.
- Create a VPC peering connection between the worker instance VPC and standard repository VPC, and accept the peering request to enable route traffic between those VPCs.
- Add routes to the route tables associated with the subnets of the worker instance VPC and standard repository VPC to enable private traffic between those VPCs.
Destination | Target |
|---|---|
Worker Instance VPC | |
Worker instance VPC (12.0.0.0/16) | Local |
Standard repository VPC (11.0.0.0/16) | pcx-zzzz |
Standard Repository VPC | |
Standard repository VPC (11.0.0.0/16) | Local |
Worker instance VPC (12.0.0.0/16) | pcx-zzzz |
- Establish a connection between the backup account and archive repository account. To do that:
- Create interface VPC endpoints required for the worker instances to access AWS services to archive backups:
- Create a VPC (for example, 13.0.0.0/16) and a private subnet in the archive repository account.
- Create an S3 interface VPC endpoint for the private subnet to which the worker instances will be connected. The endpoint will be used to access the Amazon S3 service.
- Create a security group associated with the endpoint network interface to allow inbound HTTPS traffic (port 443) from the worker instances, standard backup repository and backup appliance.
- Configure the following peering connection settings.
- Create a VPC peering connection between the worker instance VPC and archive repository VPC, and accept the peering request to enable route traffic between those VPCs.
- Add routes to the route tables associated with the worker instance VPC and archive repository VPC to enable private traffic between those VPCs.
Destination | Target |
|---|---|
Worker Instance VPC | |
Worker instance VPC (12.0.0.0/16) | Local |
Standard repository VPC (11.0.0.0/16) | pcx-zzzz |
Archive repository VPC (13.0.0.0/16) | pcx-vvvv |
Archive Repository VPC | |
Archive repository VPC (13.0.0.0/16) | Local |
Worker instance VPC (12.0.0.0/16) | pcx-vvvv |
- Establish a connection between the standard repository account and archive repository account. To do that:
- Create a VPC peering connection between the standard repository VPC and archive repository VPC, and accept the peering request to enable route traffic between those VPCs.
- Add routes to the route tables associated with the standard repository VPC and archive repository VPC to enable private traffic between those VPCs.
Destination | Target |
|---|---|
Standard Repository VPC | |
Standard repository VPC (11.0.0.0/16) | Local |
Worker instance VPC (12.0.0.0/16) | pcx-zzzz |
Archive repository VPC (13.0.0.0/16) | pcx-kkkk |
Archive Repository VPC | |
Archive repository VPC (13.0.0.0/16) | Local |
Worker instance VPC (12.0.0.0/16) | pcx-vvvv |
Standard repository VPC (11.0.0.0/16) | pcx-kkkk |
Note |
Make sure that a connection is also established between the backup appliance account and both the standard and archive repository accounts. |
- Update the security groups associated with the endpoint network interfaces to allow inbound HTTPS traffic (port 443) from the backup appliance, the worker instances, the standard backup repository and the archive backup repository.
Security Groups Associated with S3 Interface Endpoint | From | Protocol | Port | Notes |
|---|---|---|---|---|
Standard repository VPC | Backup appliance VPC (x.x.x.x/32) | TCP | 443 | Allows inbound HTTPS traffic from the backup appliance |
Worker instance VPC (12.0.0.0/16) | TCP | 443 | Allows inbound HTTPS traffic from the worker instances | |
Archive repository VPC (13.0.0.0/16) | TCP | 443 | Allows inbound HTTPS traffic from the archive backup repository | |
Archive repository VPC | Backup appliance VPC (x.x.x.x/32) | TCP | 443 | Allows inbound HTTPS traffic from the backup appliance |
Worker instance VPC (12.0.0.0/16) | TCP | 443 | Allows inbound HTTPS traffic from the worker instances | |
Standard repository VPC (11.0.0.0/16) | TCP | 443 | Allows inbound HTTPS traffic from the standard backup repository |
For detailed instructions on how to create interface endpoints, set up VPC peering connections and add routing, see Configuring Private Networks.